Password toolbox
MOBILedit Forensic Standard & PRO
MOBILedit Forensic allows you to extract iTunes backups from iOS devices and ADB backups from Android devices. You can even load historical backups that have been created previously for detailed analysis or comparison.
It is not uncommon to find backups that are protected with some form of password or a code. To analyze such a backup, a password must be obtained to gain access.
MOBILedit Forensic will prompt you to enter the backup password at the relevant stage of the extraction if the user has already set a password. However, it must be known by the examiner.
For iOS, if a password was not set by the user, MOBILedit Forensic will ask you to confirm automatically setting the backup password to “123”. This will force the encryption of the iTunes backup which contains more data than an unencrypted backup, which you would get if you do not set a password.
If you think your report is missing data, please check that an encrypted iTunes backup was acquired, this can be seen in the “Summary_full.txt” document in the report output folder.
For Android, MOBILedit Forensic will automatically enter a backup password on the device and you do not need to confirm this. Android passwords are set on an individual backup basis, iOS backup passwords are for all backups created from that device.
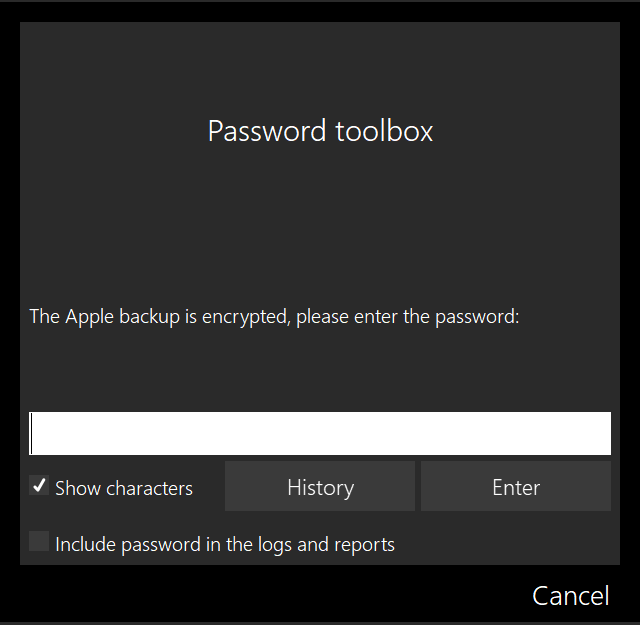
Entering password directly
The password can be entered directly if it was obtained during an investigation or, through other means. There is an unrestricted number of attempts allowed to enter the password, so you can't get permanently locked out. You can also see the history of previously entered unsuccessful passwords.
You can choose to include the password into the logs and reports.
With MOBILedit Forensic ULTRA you can brute force backup passwords. This feature was previously in MOBILedit Forensic PRO yet is now included in ULTRA due to dual-use regulations.
