Android - Rooting (Temporary)
In MOBILedit Forensic there are several methods allowing you to temporarily root the Android device. If rooting the device is successful, then our communication service with root privileges will be running on the device.
To use these methods USB debugging has to be enabled. Each of the methods is limited to certain OS versions and depends on any security patches installed on the device.
All methods can be selected automatically and MOBILedit Forensic will try one method after another, or you can choose a specific method that you know might work on the connected device. If you choose all methods, MOBILedit Forensic will stop trying further methods once a successful root has been applied.
During the process of rooting, the device can be restarted more than once. Do not use these methods if you will be not able to unlock the device after reboot.
We do not recommend disconnecting the phone after rooting until all extraction and analysis is complete. Disconnecting a device can revoke root access.
Please take note that whilst rooting is in process, don't use the device and then only if it is necessary, for example, in the case where the device will need to be reconnected after rebooting.
If there is a problem with a certain method, it can be skipped in the selection.
Please note that if all methods in the root section failed, you should try again as rooting may not be successful on the first try.
These root methods may not work for Samsung devices because of advanced security.
The Rooting section can be found in Security bypassing → Rooting
On the left side of the screen in MOBILedit Forensic, you can see basic information for each method.
Phone security patch level (SPL) criteria
Dirty COW - The vulnerability affects some Android devices without security patch levels of December 2016.
Method 1 - The vulnerability affects some Android devices without security patch levels of October 2019.
Method 2 - The vulnerability affects some Android devices without security patch levels of March 2020.
Method 3 - The vulnerability affects some Android devices based on MediaTek chipset without security patch levels of March 2020.
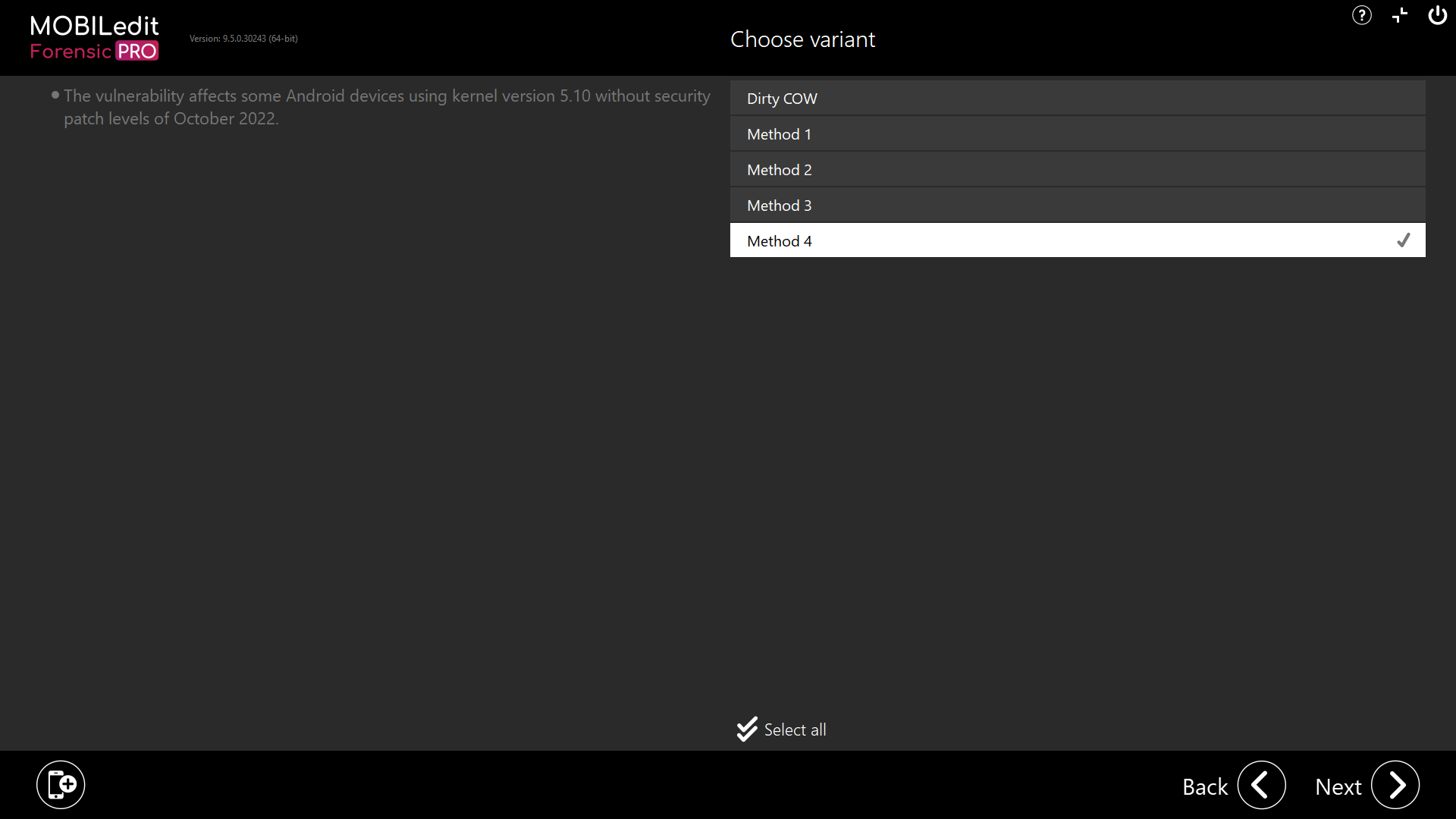
Method 4 - The vulnerability affects some Android devices using kernel version 5.10 without security patch levels of October 2022.
