Security Bypassing - Approach
Security bypassing approach
Live-connected device
Connect your device and click “Next” then all possible extraction and analysis options will be shown, including Security bypassing methods.
When a device is first connected, MOBILedit Forensic gathers some basic device details and offers a selection of choices for the operator according to the following parameters:
Device manufacturer/brand
Operating system
Chipset
Communication status (Rooted or No root access)
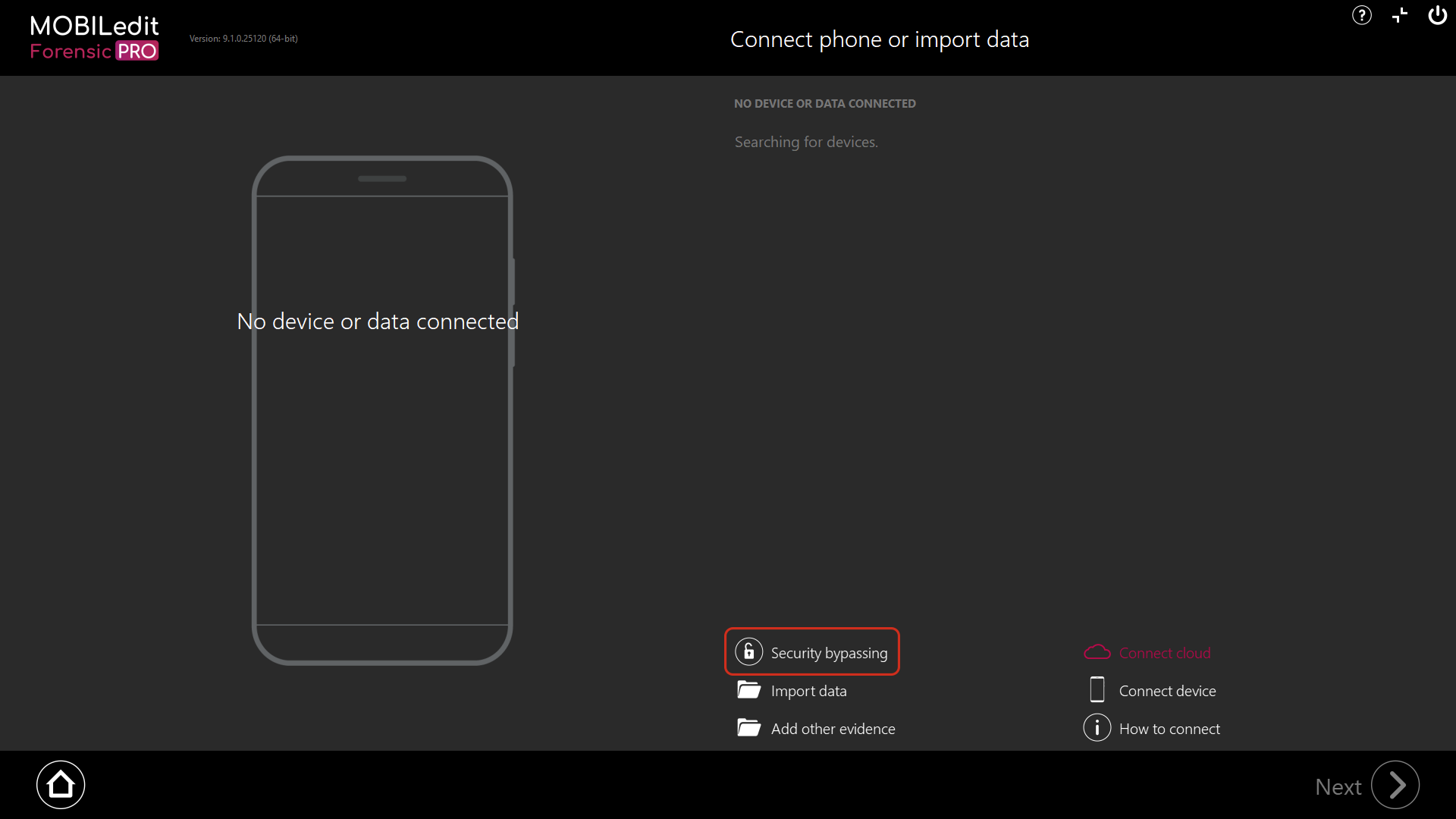
Security bypassing options
From the Home page, click “Next” and onto the “Connection screen”. Then choose “Security bypassing” and you will see the options:
By model
By Chipset
By Method
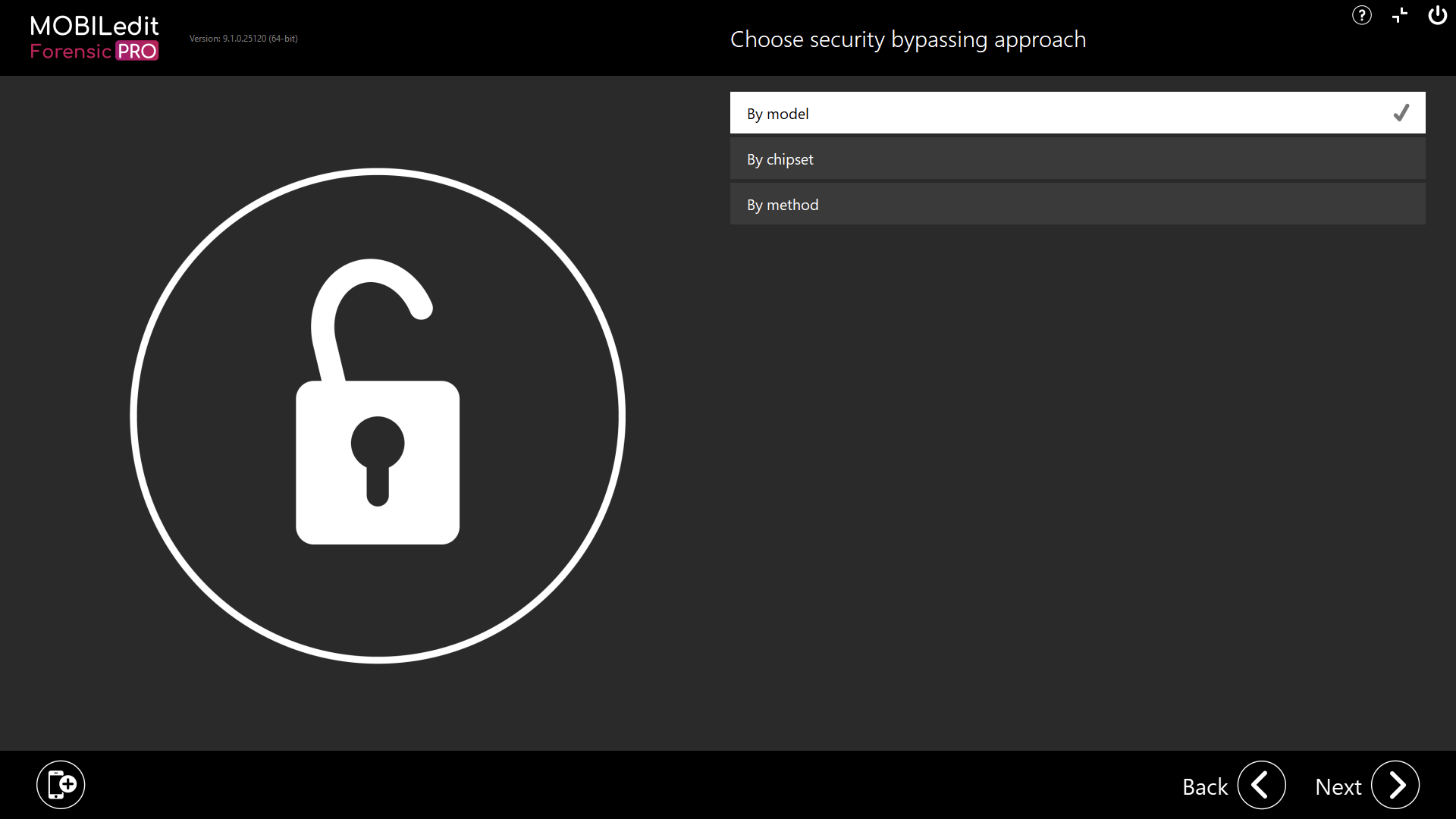
By model
Use the search field to find the exact device model from the list and after clicking “Next”, you will see all possible bypassing methods for that device. If the device is not listed, it does not mean security bypassing isn’t possible, try “By chipset”.
By chipset
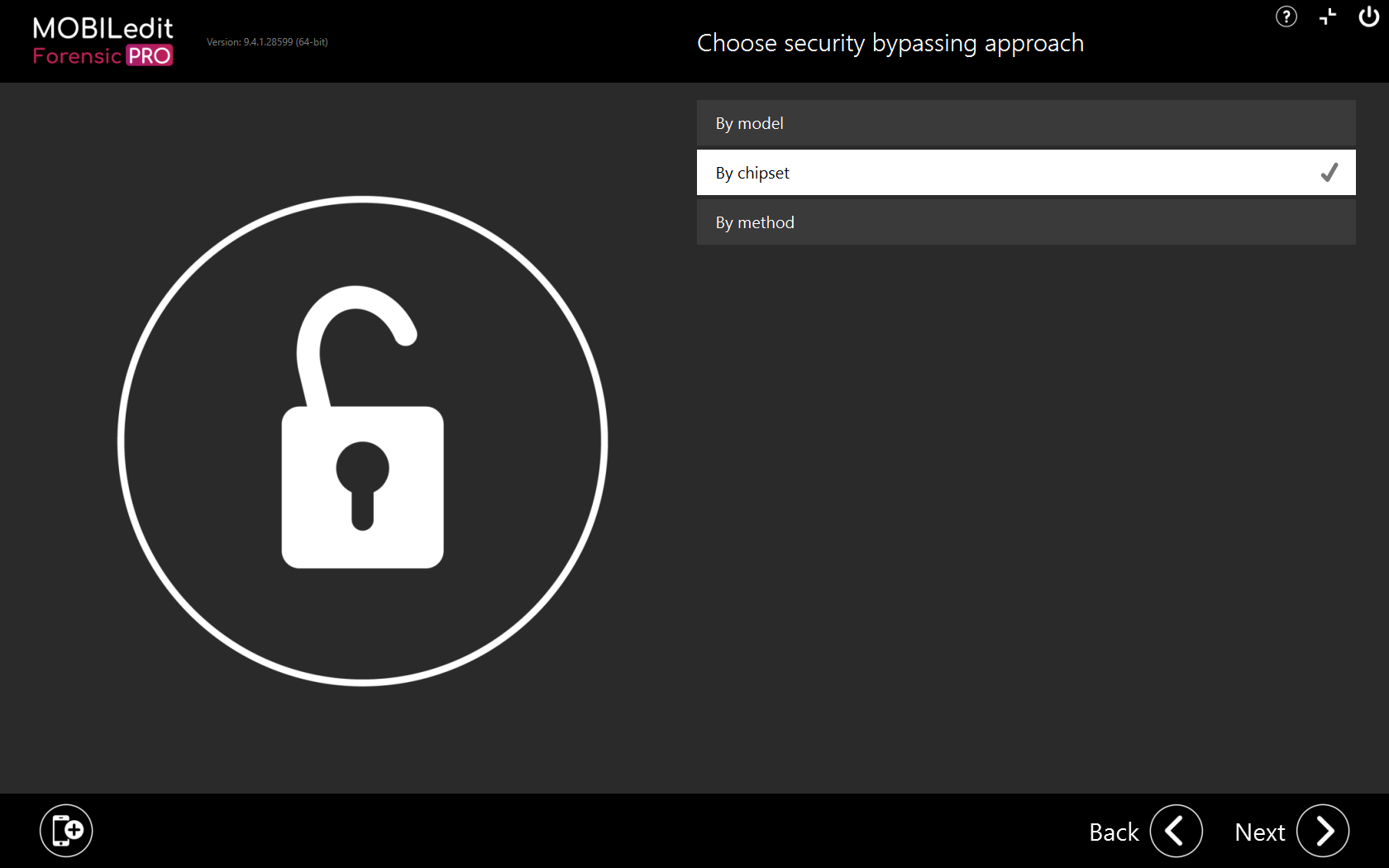
Use the search field to find the exact chipset make and model from the list and after clicking “Next”, you will see the appropriate method for that chipset.
EDL - Qualcomm,
MTK - MediaTek
Spreadtrum - Spreadtrum
Unisoc - Unisoc
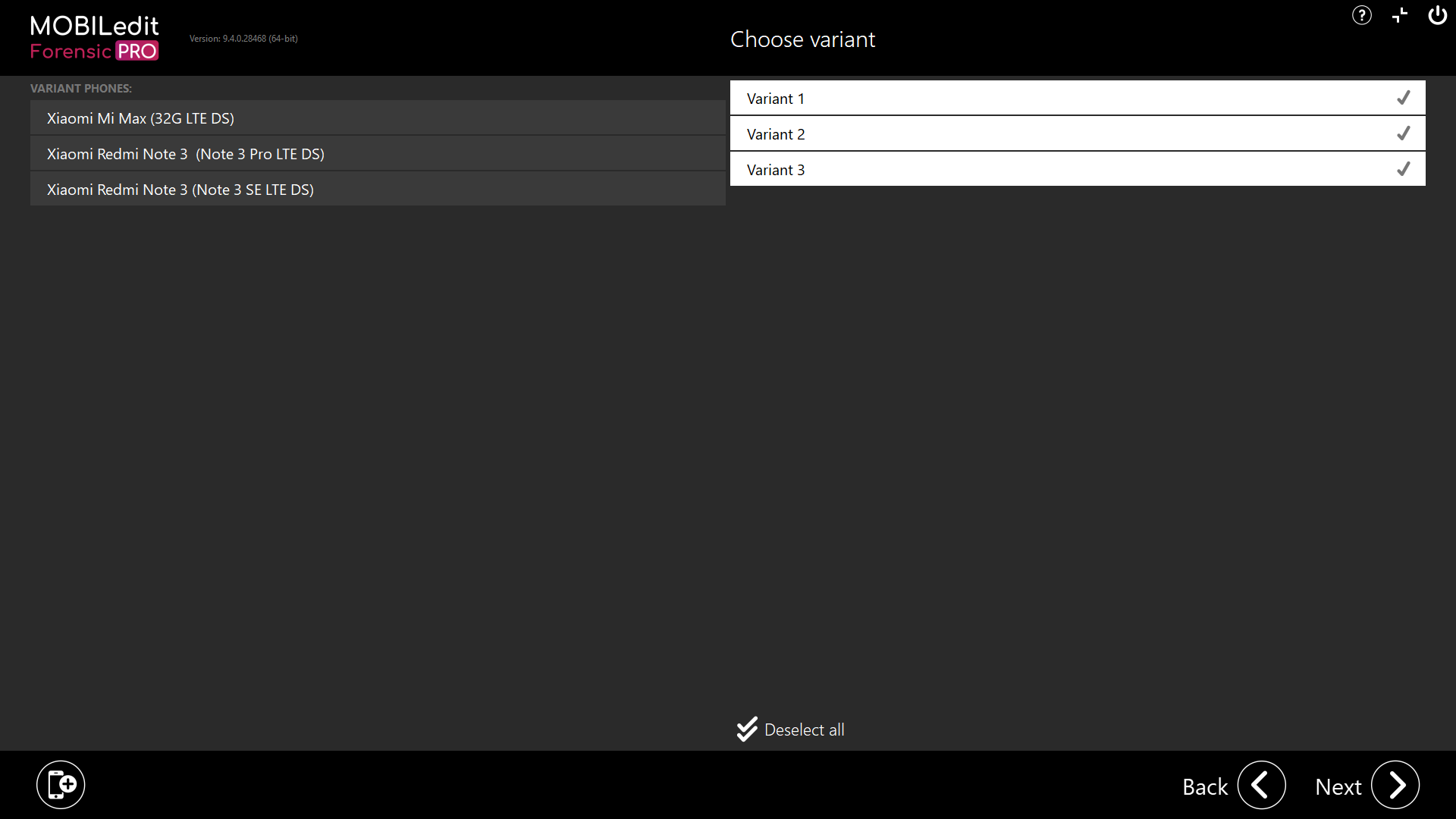
If the chipset method has more than one or multiple variants, try one at a time. Variants will be shown on the next screen and when selected, the associated device name will show on the left-hand side of the screen. We recommend choosing variants for similar types of phones.
Other chipset options for Kirin, Exynos and advanced MTK methods are available in MOBILedit Forensic ULTRA
This is a safe method as the technique runs in the RAM disk/volatile memory. Therefore, options for similar devices with the same chipset can be attempted.
By method
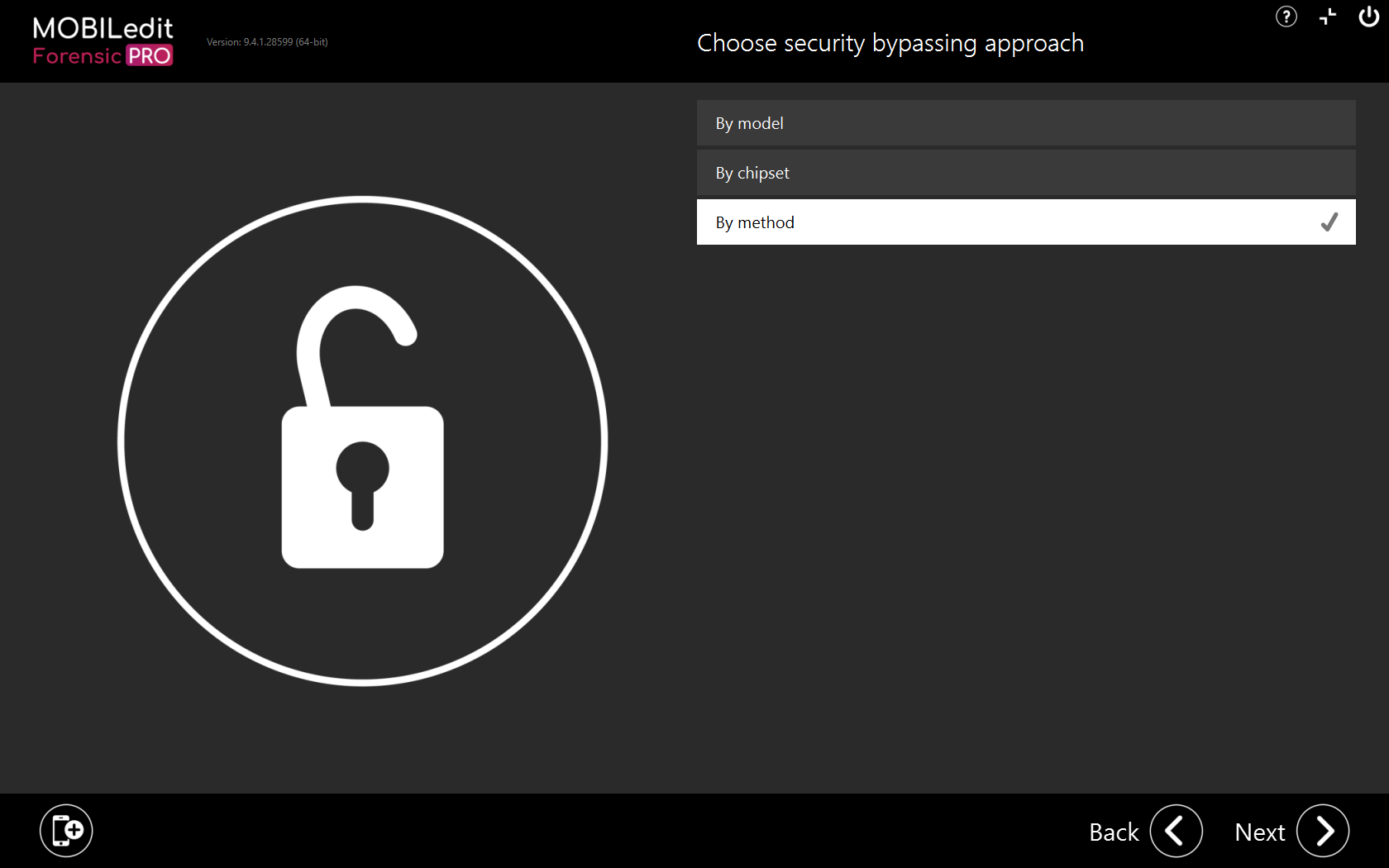
This method is intended for experienced and advanced users as in most cases, you will need to locate a device-specific file by searching the internet and other sources. All of the Security bypassing methods that are available in MOBILedit Forensic, are shown here:
such as MTK, EDL, checkra1n, rooting, etc.
This approach requires additional files, such as EDL programmers, PAC files, etc., that users must search for a specific device.
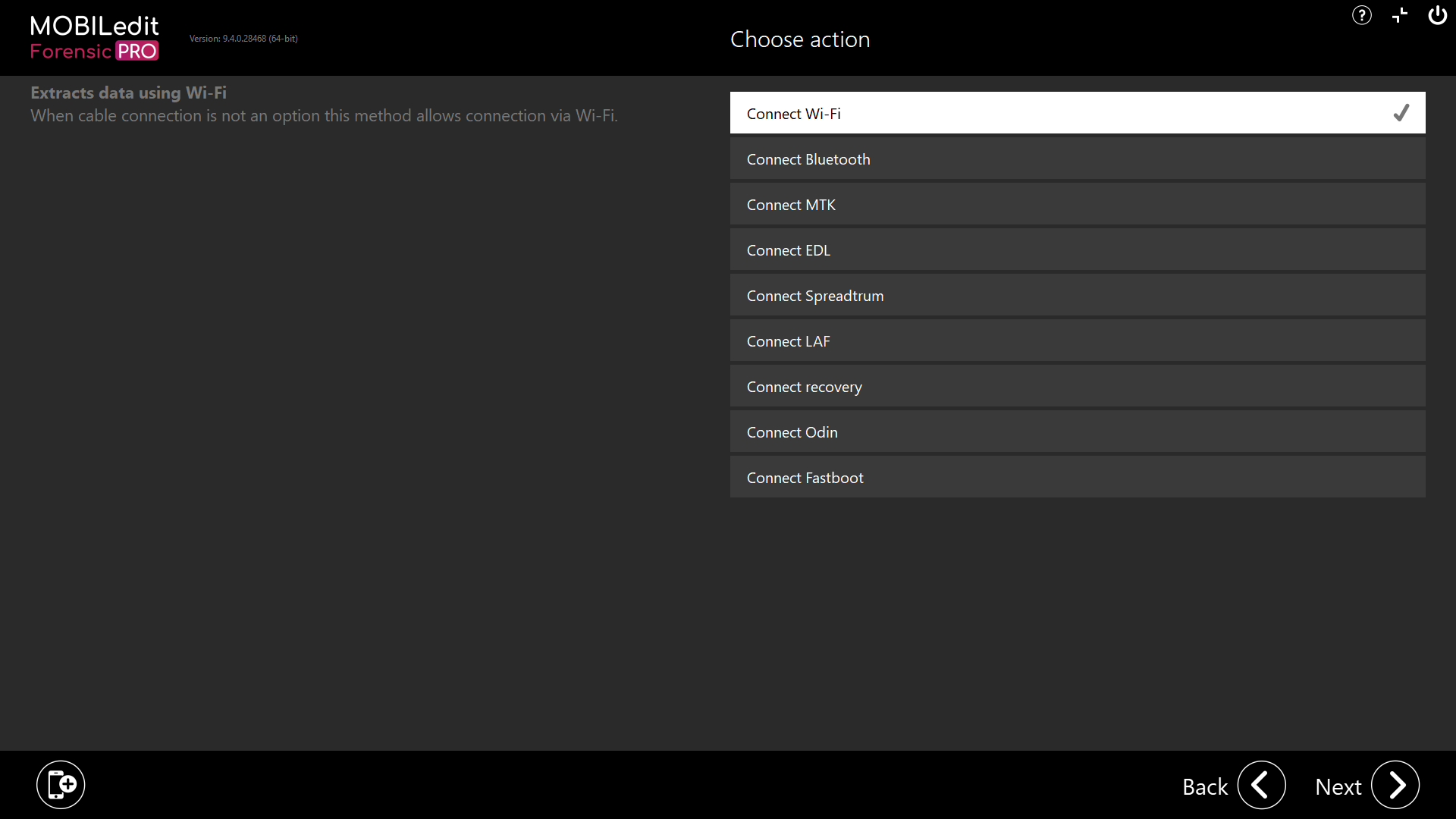
Connect device
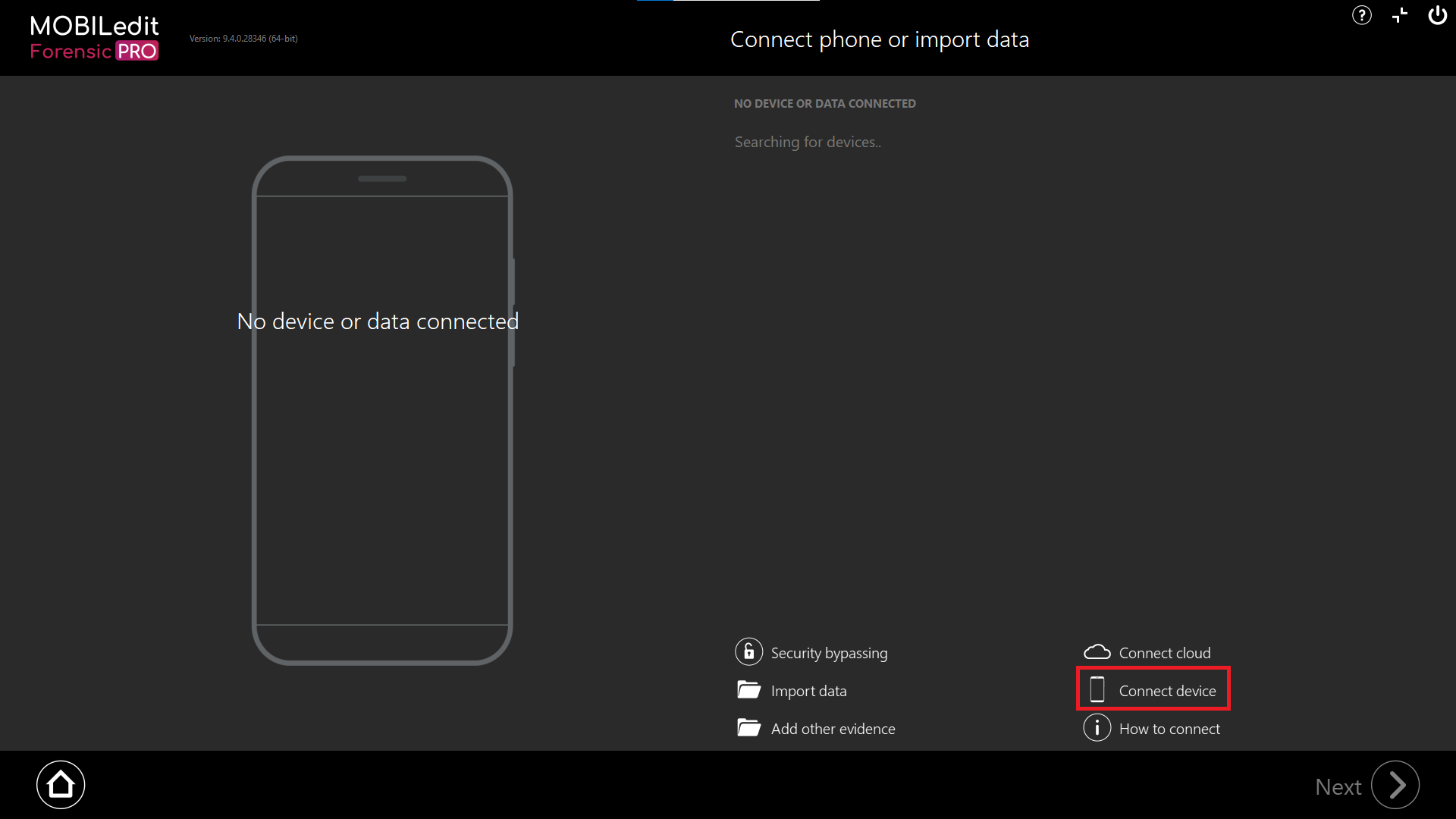
Accessing some security bypassing methods is possible from the connection screen and by selecting “Connect device”.
Connect MTK
Connect EDL
Connect Spreadtrum
Connect LAF
Connect Recovery
Connect Odin
Connect Fastboot