Mobile Device Assessment and Identification
The identification phase in mobile forensics is the initial step in the forensic process, where the user/investigator identifies the mobile device and its potential value to an investigation.
This phase is crucial because it helps determine the scope of the extraction and analysis and the specific types of evidence that may be available on the device.
MOBILedit Forensic
With a connected device that is unlocked, you will be able to access some information that is described on this page by using the following features:
“i” (information) button - Gives an overview of the device details and properties.
Browse content > File manager >Extra (applications1) > getprop.txt
These are just a few examples of what can be found in the getprop.txt document: [ro.crypto.state] = encrypted or not, [ro.crypto.type] = FDE, FBE, etc., [ro.hw.oemName] = model, [ro.hardware] = chipset.
Key elements to identify during the identification phase:
1. Mobile Device Type, Model and Chipset
Identify the make, model, chipset, and manufacturer. This is an important step because different devices have different operating systems (iOS, Android, etc.) and might require different methods for extraction and analysis.
ANDROID
There are various ways through which you can determine the make, model, chipset, and manufacturer of the mobile device:
Label
Sometimes there is a small information sticker on the back of the mobile phone that provides information like make, model, IMEI and manufacturer.

Engraving
Some smartphones have an engraving on the back of the mobile phone detailing the make, model and manufacturer.

SIM card tray
Some manufacturers imprint the IMEI number on the SIM card tray. It is always best to cross-check the number with one of the other methods, as the tray could be a replacement from another device.
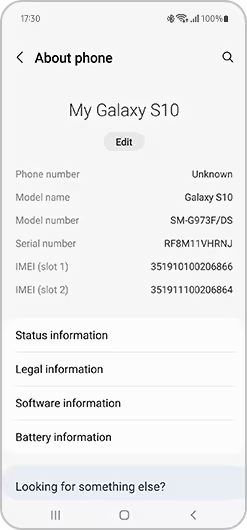
Settings
If you can unlock the phone, head to Settings>About Phone and note down the details like make, model and manufacturer and corroborate against physical identifiers and those in MOBILedit Forensic.
Google Lens
Sometimes, when the phone cannot be unlocked and when the above methods are not applicable, you can always use Google Lens to approximately identify the phone you have in question. This method requires a lot of human intervention and patience, as finding the exact make and model of the mobile phone can take time.
The majority of times, it has been found that to maximise accuracy in results, you need to scan or take a picture of the back panel of the mobile phone, as most of the time it is the differentiating factor between mobiles.
iPHONES
Engraving
The older generation of iPhones used to have engraving on the back of the mobile phone detailing the make, model and manufacturer.

Google Lens
Sometimes, when the phone cannot be unlocked and when the above methods do not apply to the device you have, you can use Google Lens to approximately identify the phone you have in question. This method requires a lot of human intervention and patience, as finding the exact make and model of the mobile phone in question can be tiring.
It has been found that the majority of the time, to maximise accurate results, you need to scan/click the picture of the back panel of the mobile phone, as it is most of the time the differentiating factor between mobiles.
Connection Ports
Newer generations of iPhone do not include engraving on the back of the phone anymore instead, the model of the mobile phone can be found using the following:
iPhone 8 to iPhone 13
-Inside the SIM card tray slot
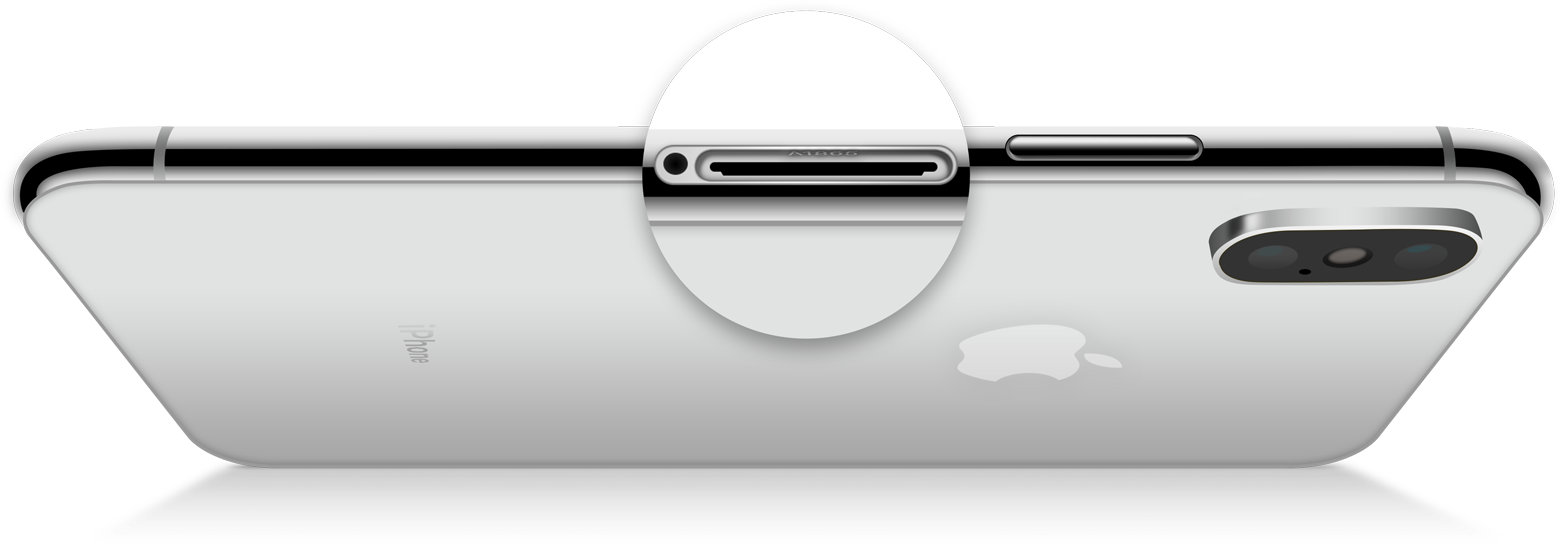
iPhone 14 to current
-Within the Charging port

2. IMEI (International Mobile Equipment Identity)
The IMEI number is a unique identifier for mobile devices, especially in GSM networks and is generally 15 digits long. Usually, the numbers are placed as follows: WW-XXXXXX-YYYYYY-Z, where:
Structure: AA-BBBBBB-CCCCCC-D
Type Allocation Code aka TAC: This code, which identifies the make and type of the device, is represented by the first eight digits (AA-BBBBBB).
Serial Number aka SNR: The unique serial number is represented by the following six digits (CCCCCC).
Check Digit aka CD: To confirm the integrity of the IMEI, the last digit (D) is the check digit. This last digit is calculated by an algorithm known as Luhn's Algorithm. Link: https://www.imei.info/luhn-algorithm/
The IMEI can be used for identification if the make & model cannot be determined by other methods. One device can have more than one IMEI number, and the number of IMEI’s found on a device is directly proportional to the number of SIM cards (whether Physical or an embedded [eSIM]). For example, a device described as dual-sim means 2 SIM cards can be inserted in the phone or you might see SIM + eSIM, both examples will have 2 IMEI numbers.
IMEI check
Find the device IMEI number, then visit the website www.imei.info and enter the IMEI number to get the information required.
Note: IMEI can be a great source of identification of a mobile phone, but the user/investigator should validate the information found using the IMEI number, as the IMEI number can be spoofed by a malicious actor, which can be misleading.
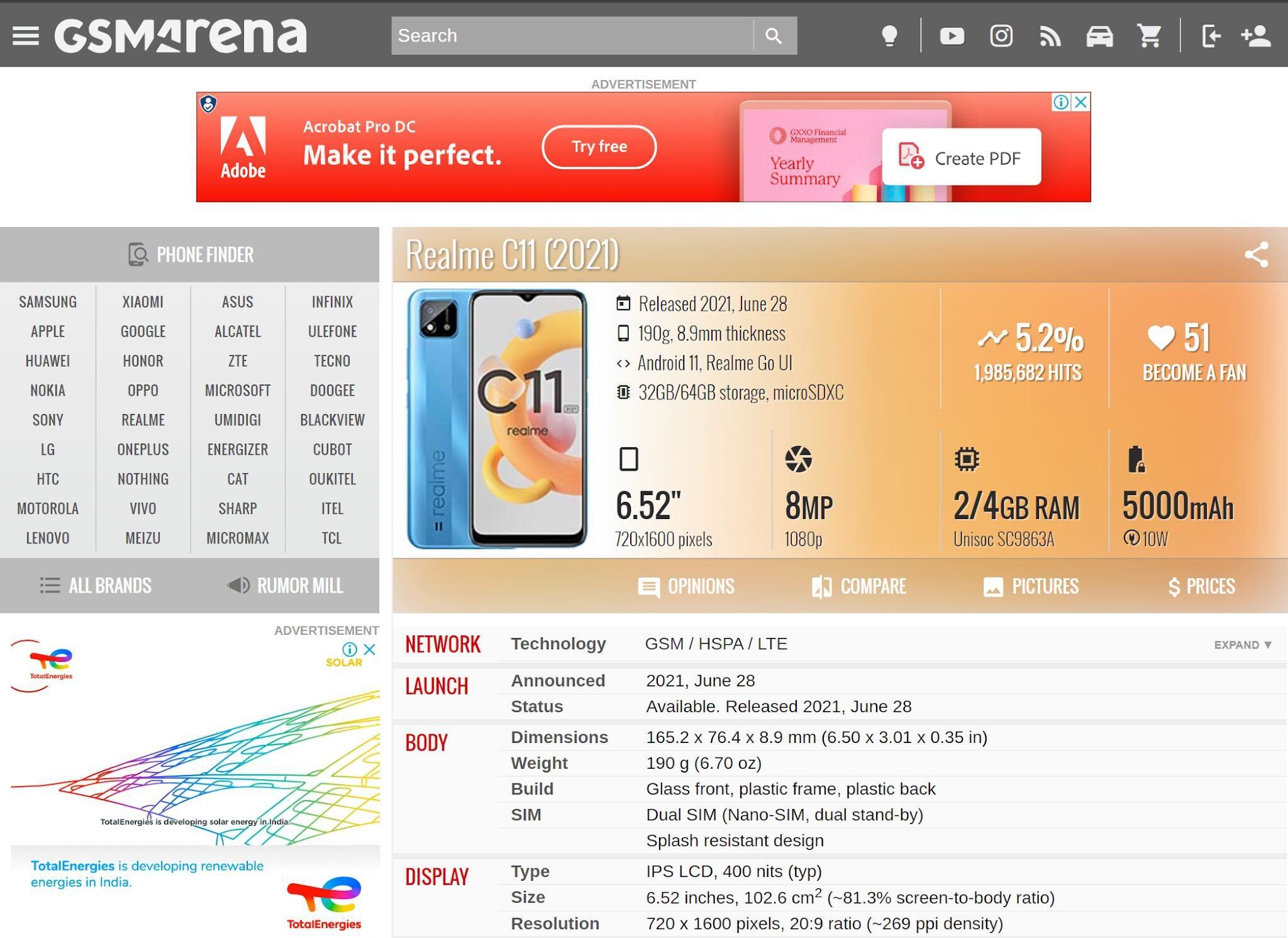
3. Internet research
Once you have utilised the above methods to get a hold of the make, model and manufacturer of the device, it is then better to go to reliable websites such as GSMArena, OEM Website, or imei.info to find out the chipset found within the device in question, especially for cases where logical extraction is not possible due to any reason. You can then apply chipset security bypassing methods within MOBILedit Forensic PRO & ULTRA.
Specifically for Apple devices, there are two useful websites: everymac.com and appledb.dev, which can be used for further model identification and also give information about what devices and iOS versions can be jailbroken.
4. Operating System (OS), Version and other important information
Determine the operating system and its version. This impacts the tools and techniques used during extraction and analysis. Different OS versions might deploy different file systems and security mechanisms.
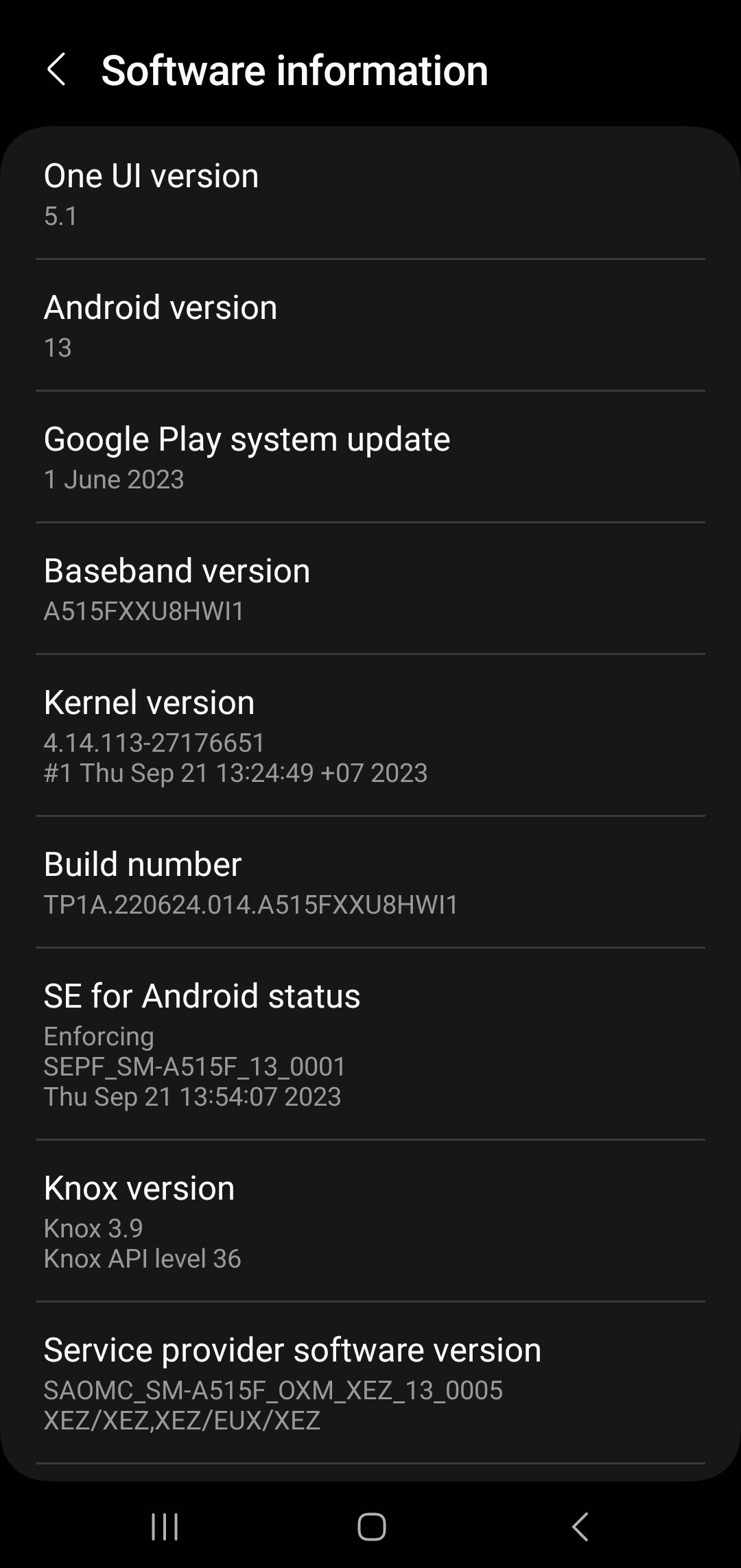
Android
You can get an idea about the current OS version and other information by going to Settings>About Phone. You should note down information like OS Version, Security Patch Level, Kernel Version, OS Skin version (E.g., MIUI Version, HyperOS Version, OxygenOS version).
iPhone
Settings > General > About
5. SIM Card Identification
If a SIM card is present, it is important to identify the SIM card’s unique identifier (ICCID) and the associated phone number. The SIM card may also hold valuable information like call logs, text messages, and contacts.
Keep SIM cards inserted during initial extraction.
Removing may trigger SIM PIN requests or lock access.
ICCID and phone number may provide key evidence and lead to further enquiries with mobile network operators.
For Apple devices, removing the SIM card will trigger the iPhone to ask for the passcode to unlock, even if the device has Face ID enabled and is in AFU mode.
6. SD Card Storage Media
Check whether the device uses removable/external memory (e.g., SD cards).
Use visual inspection or reference sources like GSMArena.
When the SIM/SD tray is removed, reinserting the SIM can trigger a PIN request.
The type, size, and presence of an SD card can:
Influence the extraction method used.
Affect the amount of data available for analysis.
Best practice: Leave the SD card inserted in the device for extraction.
SD cards are “adoptable storage”, meaning they can either be left as simple storage media or adopt the Android filesystem and become part of the internal filesystem.
Removed SD cards may be encrypted and unreadable outside the device.
The SD card often inherits the device’s encryption, making external access difficult.
During a logical extraction:
The SD card is treated as part of the device's file system.
Data from the SD card is typically included in the extraction.
During a physical image acquisition (if supported):
The SD card is not included in the physical dump.
It sits outside the internal flash memory and must be acquired separately.
7. Security Features
Identify any security features such as passwords, PINs, biometrics (fingerprint or facial recognition), or encryption that may restrict access to the data. Knowing the security setup will help plan the next steps in data acquisition, as these factors may require bypassing or unlocking techniques.
8. Potential Evidence Sources
Identify potential sources of evidence within the device that will support your investigation, such as call logs, text messages, emails, GPS data, social media apps, photos, videos, browser history, and other application data.
Research the device on the internet to see what type of artefacts the device is capable of generating.
Understanding what types of evidence may be present will inform the extraction and analysis process.
9. Physical Condition
Assess the physical condition of the mobile device, including any damage, water exposure, or other issues that may affect data extraction. This also involves identifying if the device is powered on, off, or locked.
Are the connection ports functional, and does the device have Wi-Fi and/or Bluetooth capability?
This should be considered for the extraction and the isolation of the device from the network.
You may have to find procedural workarounds or carry out hardware repairs.
The investigator can proceed to data collection and analysis when these components have been discovered. Proper identification guarantees that the evidence collected is legitimate, pertinent, and acquired following the correct forensic procedures.
