Unisoc & Spreadtrum - Get Physical dump from Unisoc
Intro
This method was previously named “Spreadtrum” and has now been named “Unisoc”
The Unisoc method extracts a physical image from phones that use Unisoc or Spreadtrum chipsets without needing root access and bypassing the lock screen. Using the SPD bootloader mode (SPD), MOBILedit Forensic accesses the phone memory through the System on Chip (SOC).
Spreadtrum chipsets are manufactured by UNISOC.
Many devices that run on the KaiOS operating system use a Unisoc or Spreadtrum chipset. The only way to get data from KaiOS devices using MOBILedit Forensic is with one of the chipset methods like Unisoc, acquiring a physical image, and re-importing the physical image for logical extraction and analysis.
Please note that the physical image is as big as the full phone storage and may be encrypted.
If it is encrypted, MOBILedit Forensic will not allow it to be re-imported.
Approach
The Unisoc method can be accessed via:
A live-connected device and choose “Next”.
Security bypassing option on the “Connect devices or import data” screen:
By model
By chipset
By method
“Connect device” option on the “Connect devices or import data” screen
To read more about these options, visit the “approach” page.
SPD bootloader mode (SPD)
Unisoc method is a way of extracting physical images from phones with Unisoc or UNISOC chipsets. This option does not require the phone to be rooted and works on most Unisoc/UNISO-equipped devices once the device is in SPD mode.
Every device has a specific way to enter SPD mode:
Handset key combination
Test points (See image below)
You must install the “Unlocking drivers” for Windows to communicate with the device in SPD mode.
You must also have the Security bypassing and Unisoc packages installed.
Using the “By model” option, a photo detailing the location of test points for a device might be shown, if the test points are known to us. This is the best approach as test point photos are not shown elsewhere.
Where shorting of the test points is required to enter SPD mode and, we have previously tested that specific device, we provide graphical instructions within the software to assist you. Below is an example of the location of the test points on a phone's printed circuit board assembly.

HOW TO
Whatever “approach” you choose to access the Unisoc method, you will ultimately reach the screen below where there is a reminder of the prerequisites, connection steps and how to enter SPD mode:
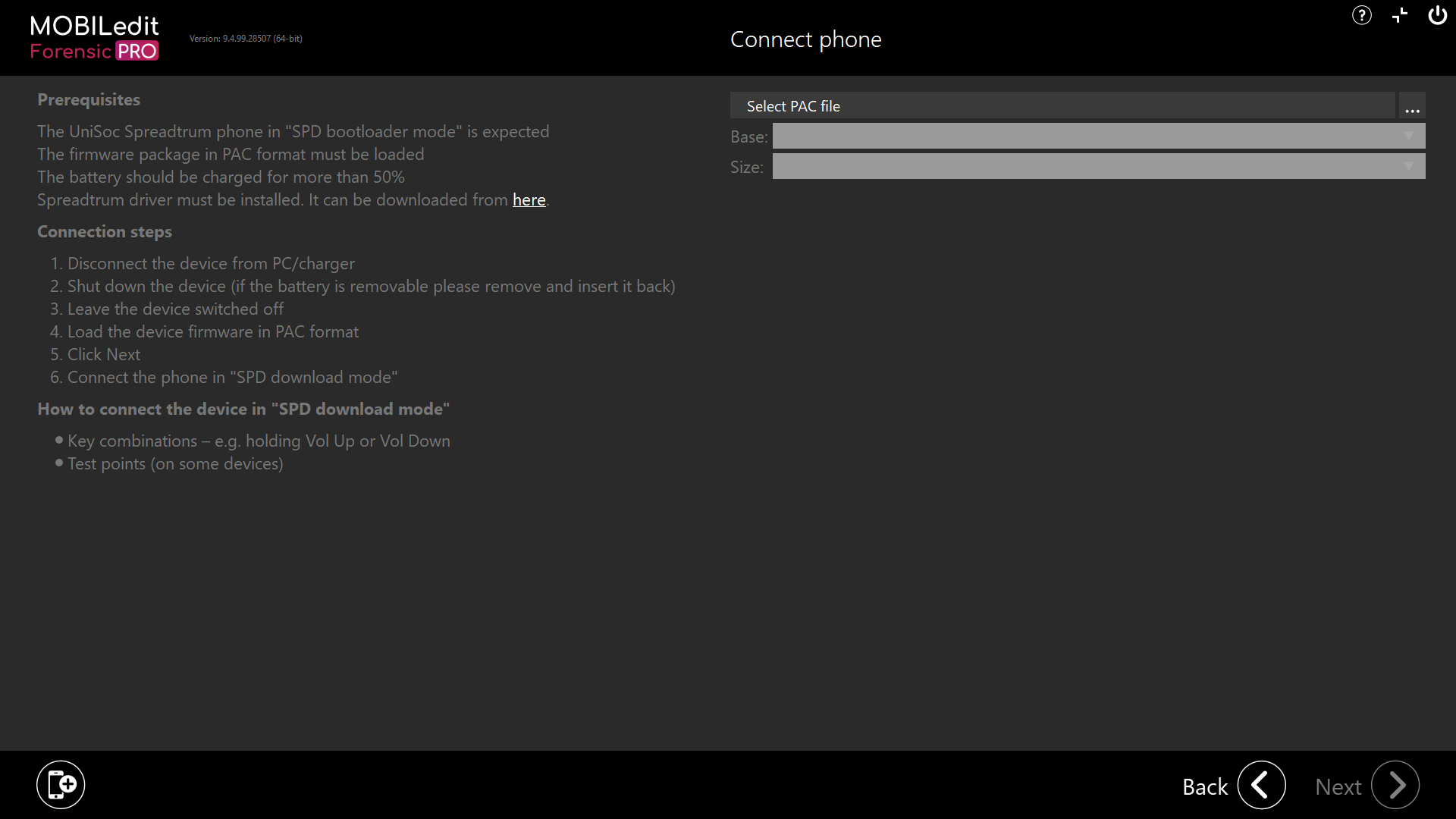
If MOBILedit Forensic does not have a preinstalled PAC file for your device, you can search for a file on the internet.
Once found, choose "Select PAC file" and import the file to MOBILedit Forensic using the three dots. Then after selecting the file and clicking “Next”, connect the phone in SPD mode, if the PAC file is correct, a physical image will be extracted.
We recommend looking for a PAC file for the phone you are investigating however, a PAC file for a similar phone or chipset may also work.
There is no risk of data loss when trying different PAC files.
Other info
There are videos online that show how to create a PAC file, you can find them on YouTube, Vimeo or other sources.
