Jailbreaking with palera1n
MOBILedit Forensic - Security bypassing > By method > palera1n
MOBILedit Forensic does not automatically jailbreak devices using palera1n, we offer and include full instructions within the user interface by selecting Security bypassing > By method > palera1n.
There are step-by-step instructions to show how it looks when running palera1n using the live Linux distribution.
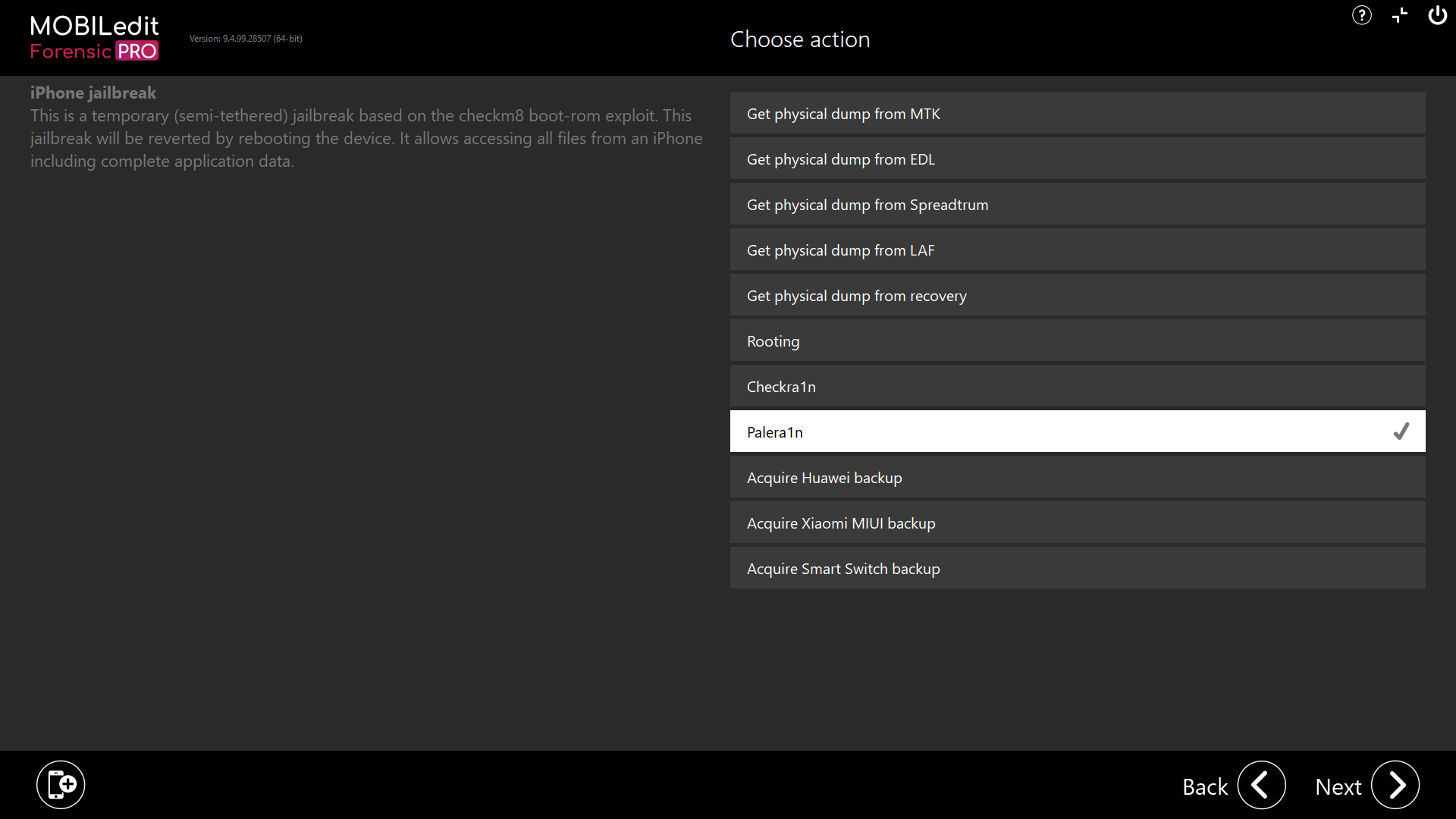
How to use Palera1n
Prerequisites:
Bootable USB Flash Disk with palera1n Jailbreaking Capability: Available in the MOBILedit Forensic Connection Kit version 10 or higher (includes both checkra1n and palera1n). For kits up to version 9, only checkra1n is included. Alternatively, you can create your own bootable Linux USB flash disk with palera1n.
Apple Device Compatibility: Devices with A8 to A11 Bionic chipsets running iOS/iPadOS versions 15.0 to 18.0.
USB Cable: Compatible USB cable to connect the Apple device to your computer.
Computer Requirements: A computer with an Intel processor, capable of Legacy booting from a USB flash disk.
How to Use the Bootable USB Flash Disk with palera1n Jailbreaking Capability:
Prepare Computer BIOS:
Ensure your computer's BIOS is set to boot from USB (Legacy external device boot: USB storage device, Secure Boot disabled).
Insert USB Flash Disk:
Insert the USB flash disk into a USB port of your switched-off computer.
Boot from USB Flash Disk:
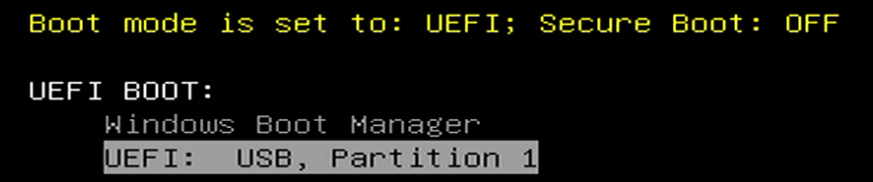
Restart your computer and boot from the USB flash disk (select: Legacy external device boot: USB storage device).
Note: For example, on Dell computers, you can access the one-time boot menu via F12 when starting the system. Then from the UEFI BOOT: menu select the UEFI: USB, Partition 1
Bootra1n Screen:
On the Bootra1n screen, select "Void Linux (USB Safe)" and press Enter.

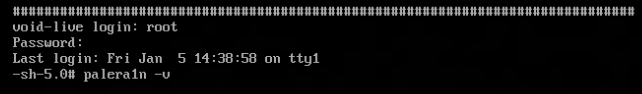
Login Details:
void-live login: root
Password: voidlinux

Connect Apple Device:
Connect the Apple device in normal mode via USB. Confirm trust on the Apple device screen. Ensure your Apple device is connected to the USB port before proceeding to the next command.
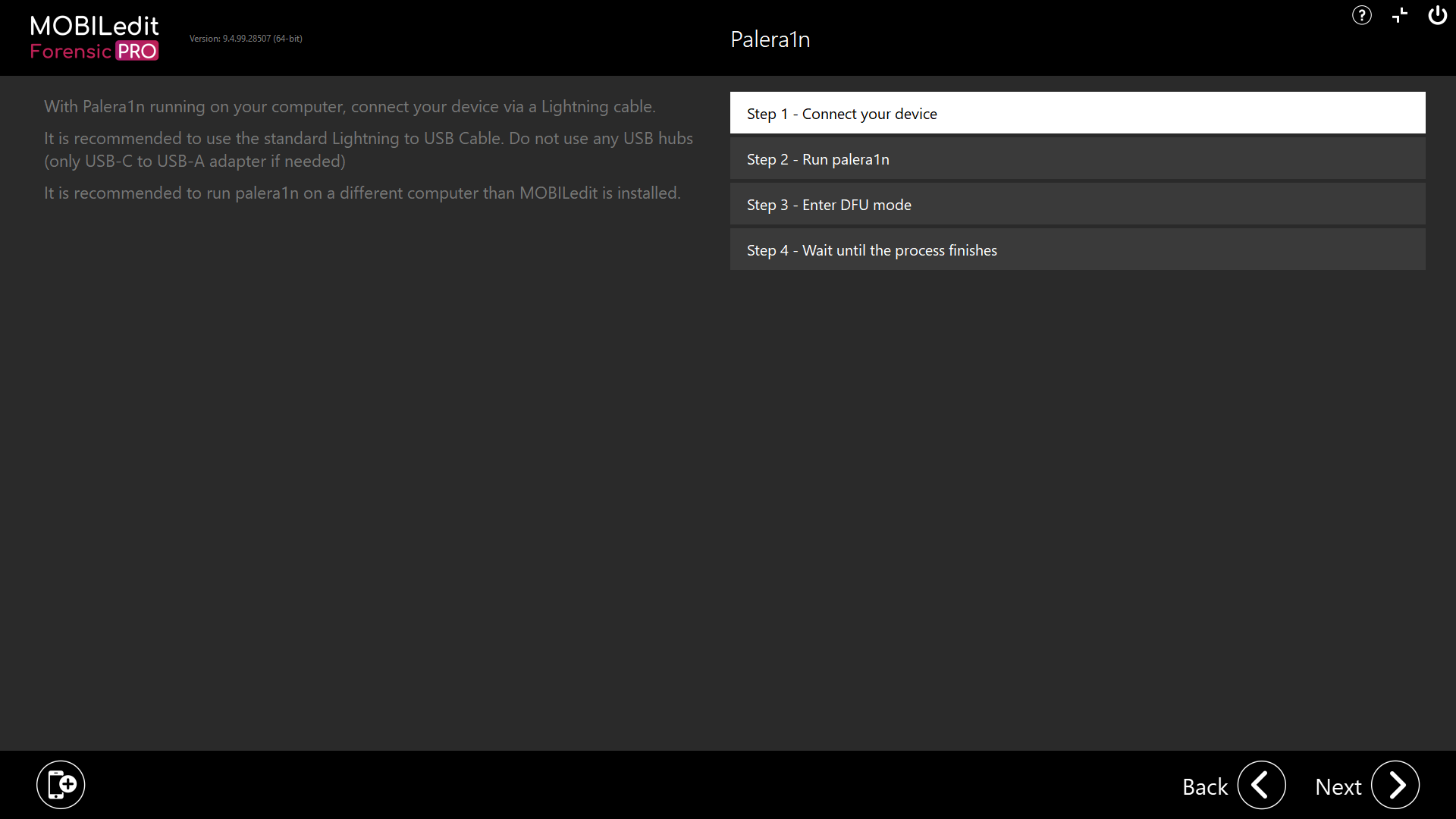
Run palera1n:
Execute the command: palera1n -l -v
palera1n will automatically put the device into recovery mode.
Enter DFU Mode:
Press Enter when prompted for DFU mode.
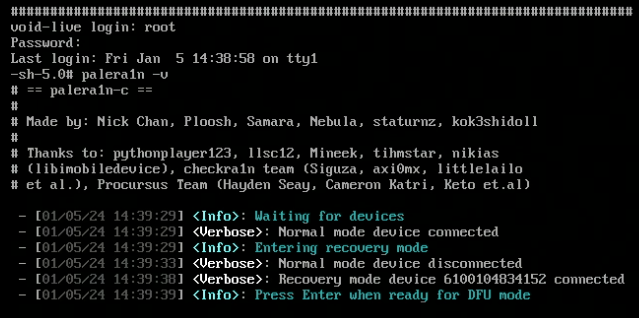
Follow the on-screen instructions for pressing and releasing specific buttons on your Apple device (varies by device model).
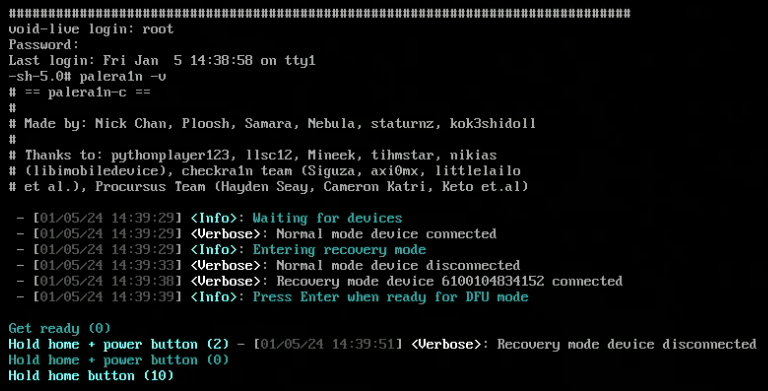
palera1n will then restart the device into DFU mode, execute the exploit, boot the kernel, and start the jailbroken iOS.
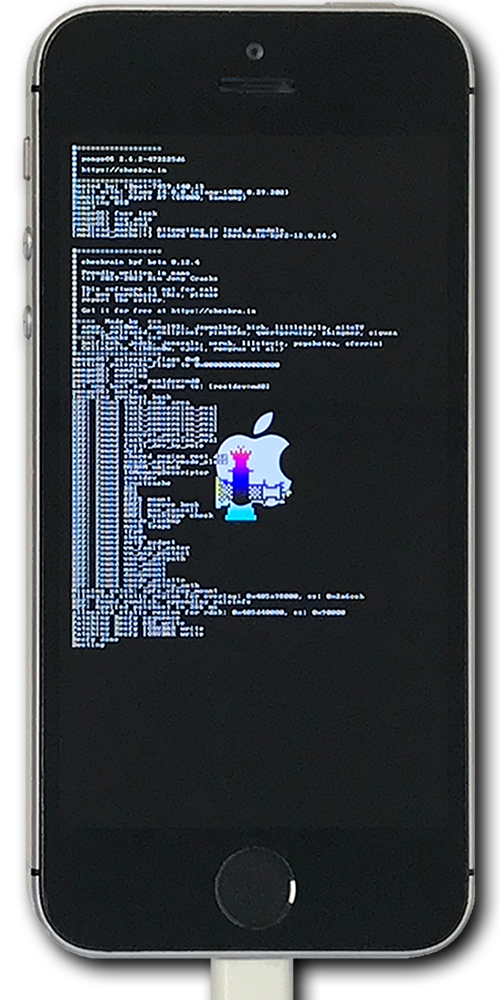
Completion:
Your device is now jailbroken.
For a jailbroken device to successfully connect to MOBILedit Forensic, Apple Mobile Device Service must be enabled on the workstation.
This can be achieved by having iTunes installed on the workstation. To obtain the correct installation package, use this direct link "Download iTunes for Windows now (64-bit) - apple.com" and do not use the iTunes provided through the Microsoft Store.
How to check if a specific device is jailbroken using palera1n:
the palera1n icon is visible on the device screen

and
When the device is connected correctly and is recognised by MOBILedit Forensic, the text "JAILBROKEN" is visible under the photo of the connected device and the "Rooting status" in "Phone Info" is "SSH".
How to remove the palera1n jailbreak from the device
The palera1n jailbreak is semi-tethered and runs only in the RAM of the device. Once you have completed all the analysis and want to remove the jailbreak from the device, just restart or shut down the device. When you restart or shut down the operating system, the device will no longer be jailbroken.
Please ensure that these instructions are used in compliance with legal and ethical standards, especially considering their application in digital forensics and law enforcement contexts.
