MTK - Get Physical dump from MTK
Intro
The MTK method extracts a physical image from phones that use MediaTek chipsets without root access and bypassing the lock screen. Using the preloader or BROM (Boot ROM) modes, MOBILedit Forensic accesses the phone memory through the System on Chip (SOC).
Please note that the physical image is as big as the full phone storage.
Approach
The MTK methods can be accessed via:
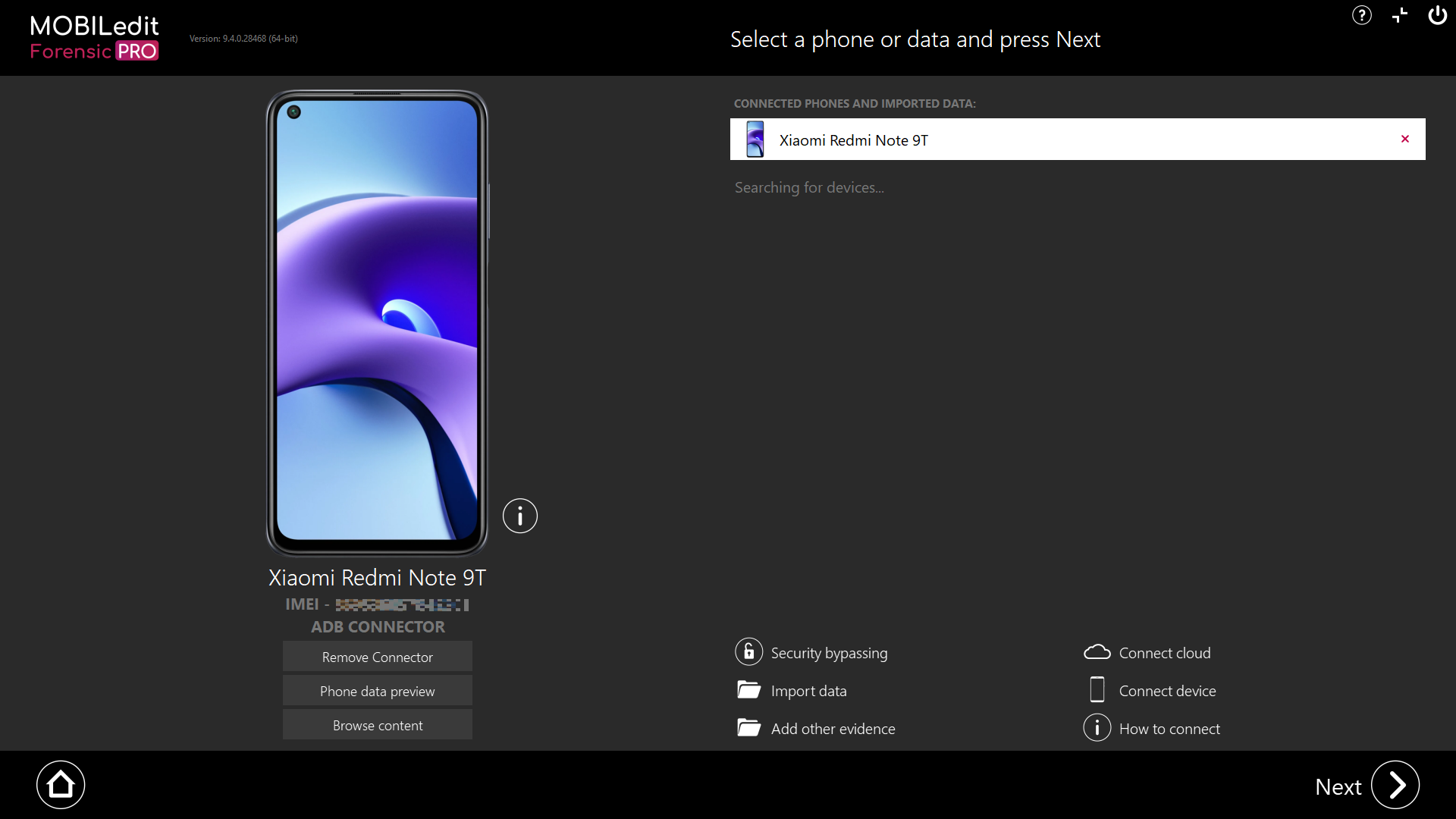
A live-connected device and choose “Next”.
Security bypassing option on the “Connect devices or import data” screen:
By model
By chipset
By method
“Connect device” option on the “Connect devices or import data” screen
To read more about these options, visit the “approach” page.
When using the “By model” option it may be possible to see a photo detailing the location of test points for a device if the test points are known to us.
Previously, it was possible to select MTK download agent .bin files to try and gain access for a physical extraction. There were 5 options of which you could choose one, more or all. These are no longer available as an option in the UI as a new MTK method has been developed.
Communication modes
Boot ROM (BROM) mode
MTK method is a way of extracting physical images from phones with MediaTek chipsets. This option does not require the phone to be rooted and works on most MediaTek-equipped devices once the device is in BROM mode. BROM is a low-level HW access mode and is used to bypass more security features.
Some devices may need to be in pre-loader mode.
Every device has a specific way to enter BROM mode:
Handset key combination
Test points (See image below)
Connect the device to a computer in a powered-off state
When in BROM mode, the device identifies itself as “MediaTek USB Port” in the Device Manager.
You must install the “Unlocking drivers” for Windows to communicate with the device in BROM mode.
If the connection is unsuccessful and you want to make another attempt, boot to the system and power off again before retrying.

Honor 8S_KSA-LX9
Preloader mode
Compared to BROM, this mode is a higher-level access mode that works on older devices with MediaTek chipsets that could previously use the download agents for security bypassing with the MTK method.
To enter into preloader mode you should follow these steps:
Have the device charged to at least 50%
Power off the device
Remove the back of the device and disconnect and reconnect the battery.
When ready, connect the phone and it will automatically set to preloader mode and MOBILedit Forensic will continue the process.
How to
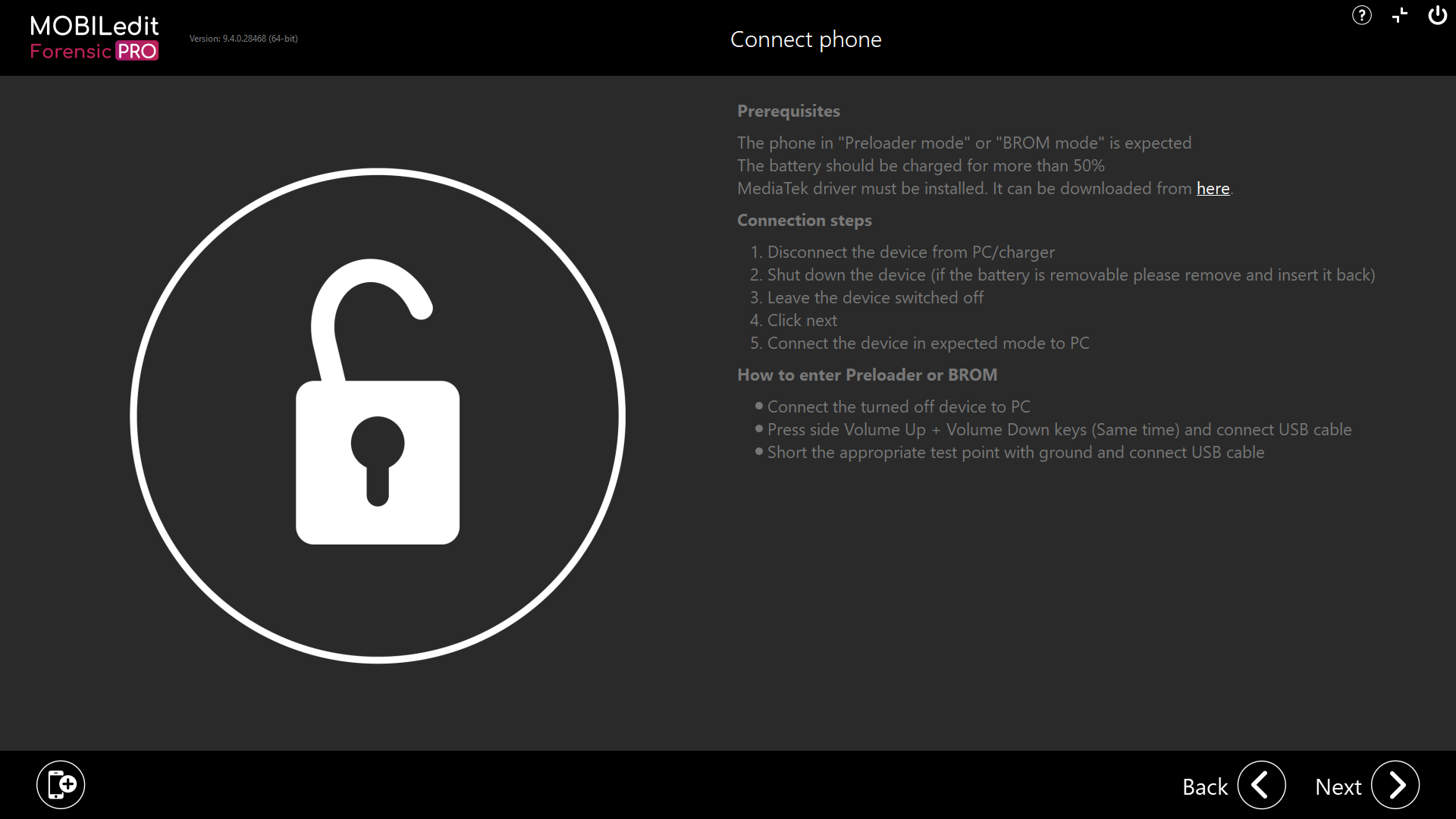
Whatever “approach” you choose to access the MTK method, you will ultimately reach the screen below where there is a reminder of the prerequisites, connection steps and how to enter BROM or preloader modes:
To show the method in full, we will use a live-connected device and select “next”
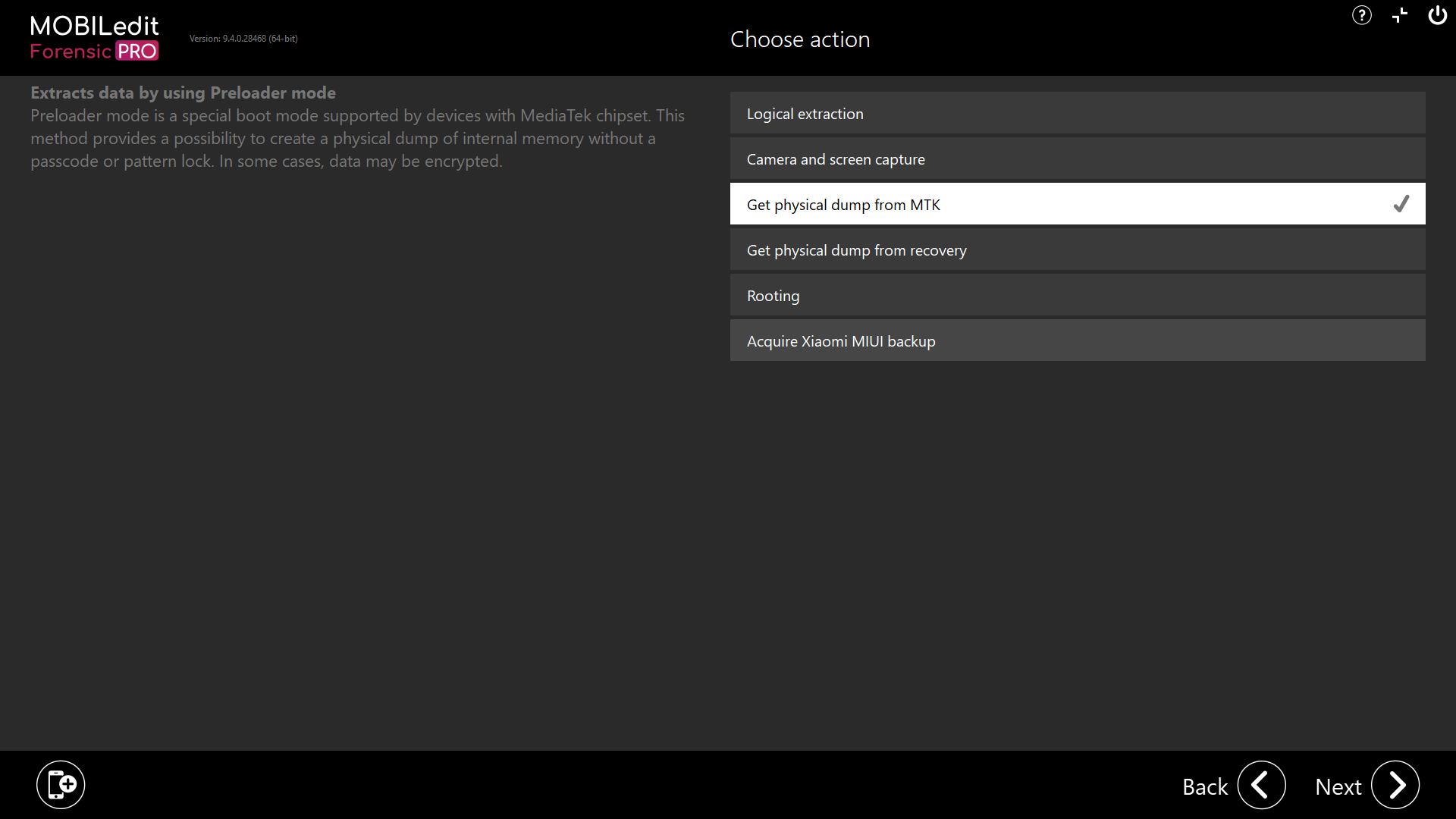
You will see all available options for the connected device and select “Get physical dump from MTK”.
Now carefully read the on-screen instructions to disconnect the device and set it to preloader or BROM mode.

The options under “How to enter Preloader or BROM” are all ways that it might be possible to get the device into the correct mode.
Always start with BROM and the “Press side Volume Up + Volume Down keys (Same time)…”, Click next and then connect the device via USB cable.
If unsuccessful, try the other methods.
Select Next and re-connect the device and it will enter into BROM or Preloader mode
If it is possible to use this method with the connected device, the physical will be extracted.
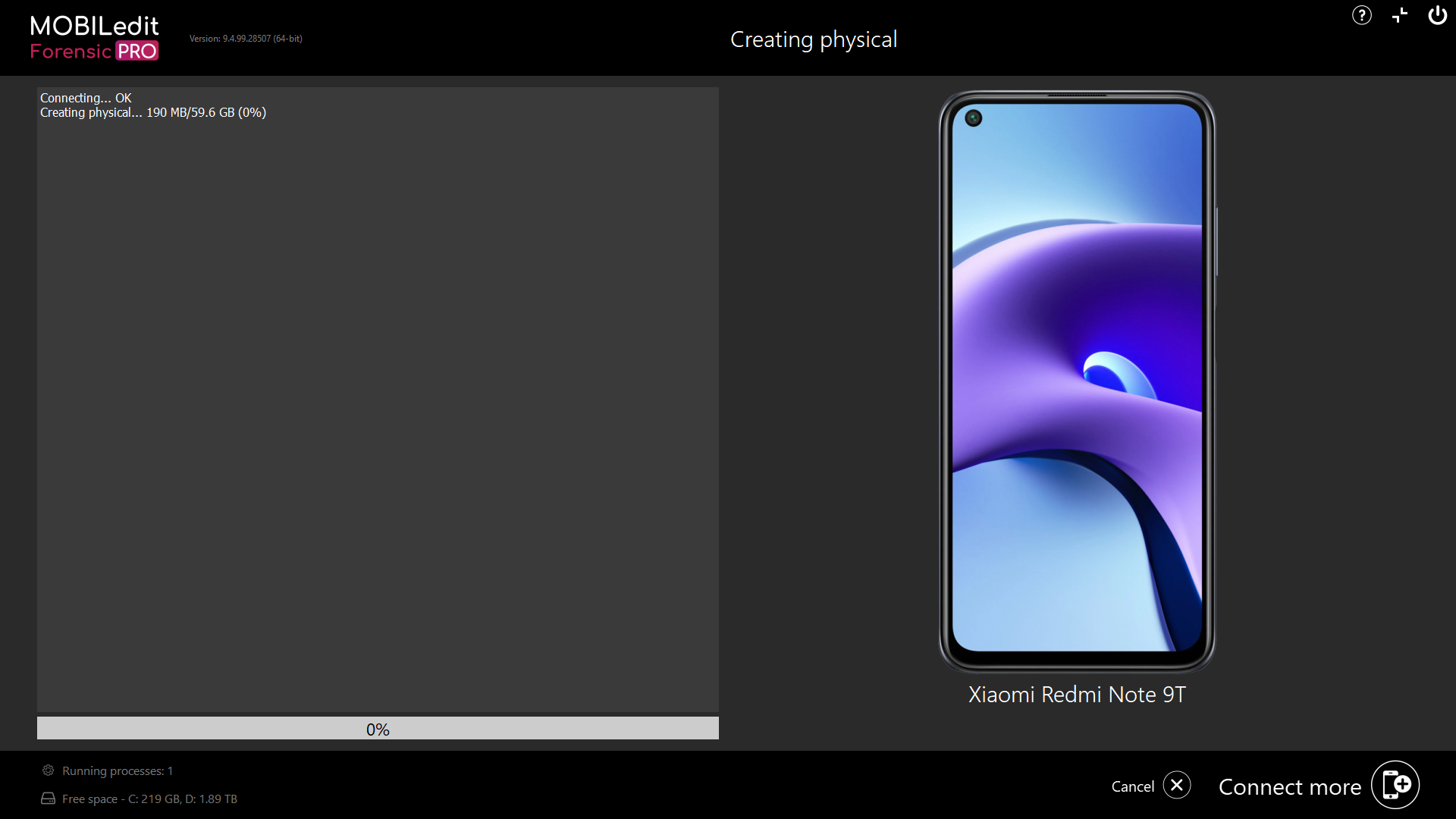
Once complete, MOBIledit Forensic will attempt to automatically load the physical image for a logical extraction and analysis of the newly extracted physical image.
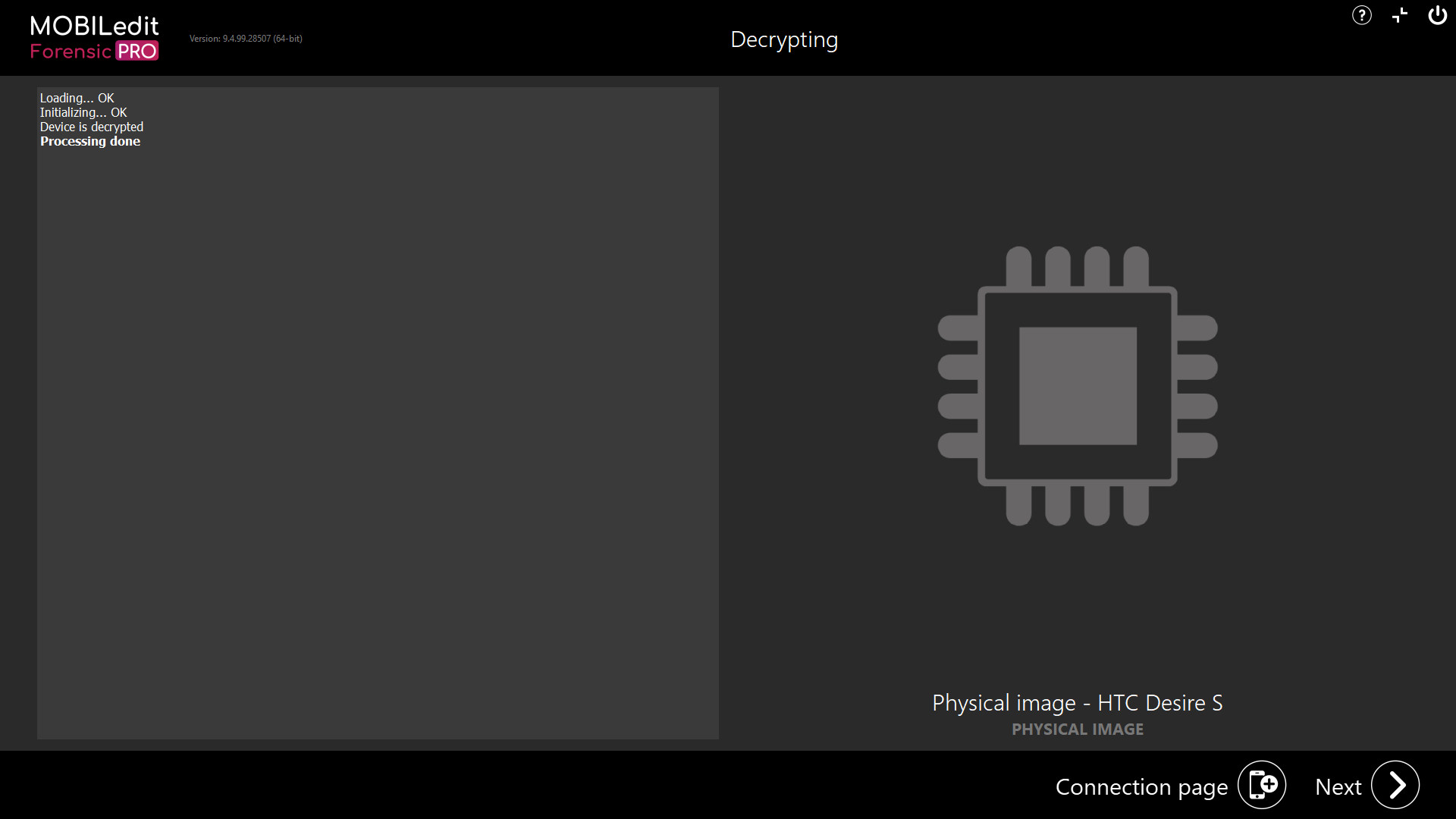
If the physical image uses encryption, it will fail to load as the HW keys cannot be extracted with MOBILedit Forensic PRO. To load and decrypt the physical image, you must use MOBILedit Forensic ULTRA.

When the physical image is acquired using PRO and is encrypted, it would still be possible to connect the device with ULTRA in the future, extract the keys, load the original acquired physical from PRO, and decrypt the image.
The physical image will be saved in the report output folder:
Other
To identify what type of encryption the device is using, please visit this page:
If you are using MTK method and your device is not supported through live connection or “By model”, you can try the “By chipset” approach for the same or a closely matched chipset. This method is safe and will not harm the data or device itself.
