iTunes backup (Extraction)
MOBILedit Forensic uses iTunes backup for extracting data from iOS devices.
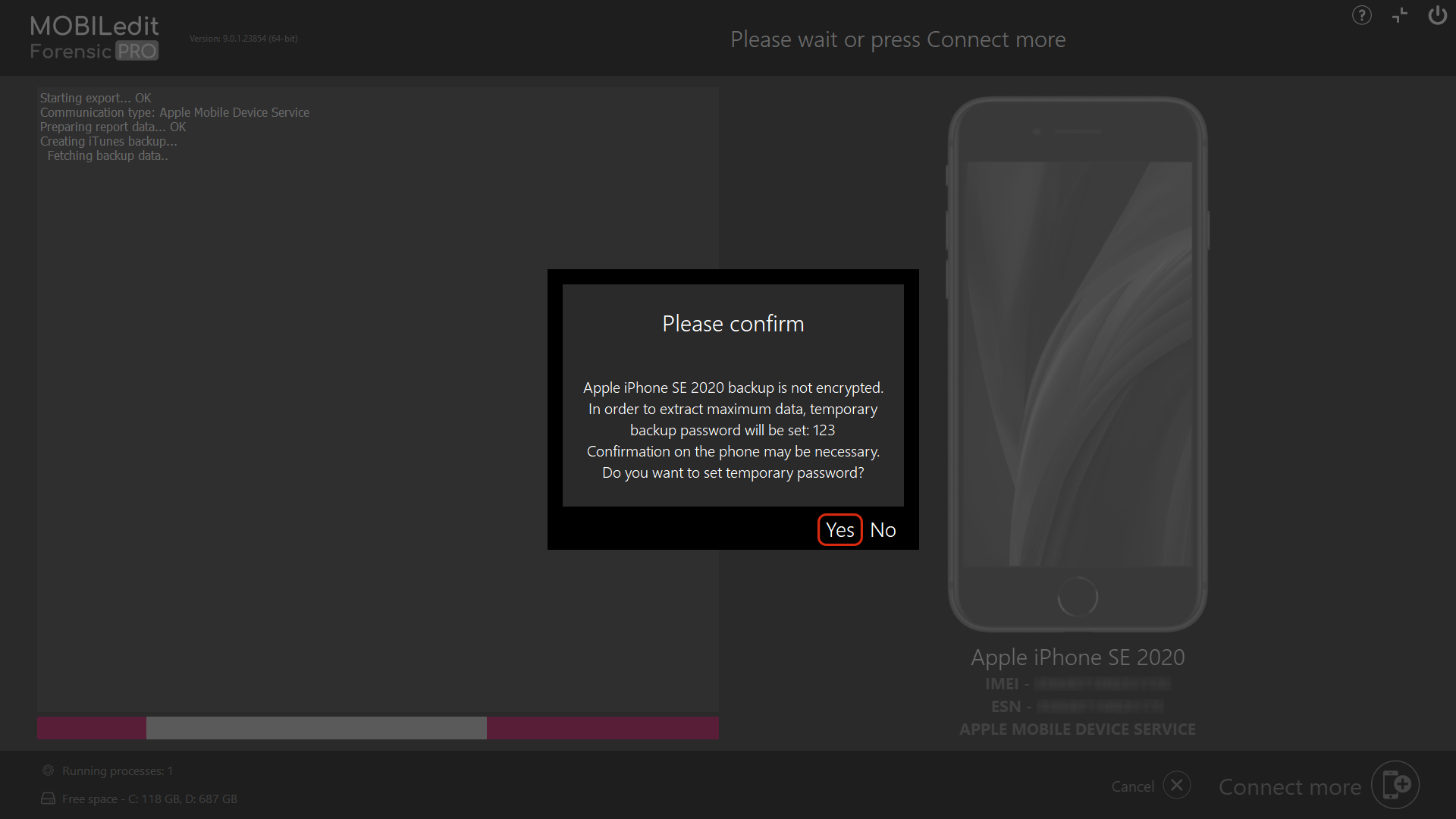
To extract as much data as possible, it is necessary to create an encrypted iTunes backup by setting a password/PIN if the device user has not already set one.
If a password is not entered, the backup will be unencrypted and contain less data.
If the device user has already configured the iTunes backup to be encrypted by previously setting a password, it is necessary to know the user's password. MOBILedit Forensic PRO will prompt you to enter the iTunes backup password if known.
It is possible to remove the backup password with an unlocked device by selecting Settings > General > Transfer or Reset iPhone > Reset > Reset All Settings.
This resets network, keyboard, location & privacy settings, etc., and removes the device’s reference to the old backup password, allowing you to create a fresh encrypted backup with a new password.
You must have the appropriate authority to do this, and you will lose the opportunity to extract certain data.
Some users do not set an iTunes backup password, but if they do, it may be the same as the PIN if you are lucky.
If no password has been set, MOBILedit Forensic will inform you that the iTunes password will be temporarily set to “123”. It will be removed after the extraction is complete.
The reason is that encrypted iTunes backup contains more data.
From iOS 16.1. the iTunes backup may need to be confirmed on the device by entering the device’s lock screen PIN/password.
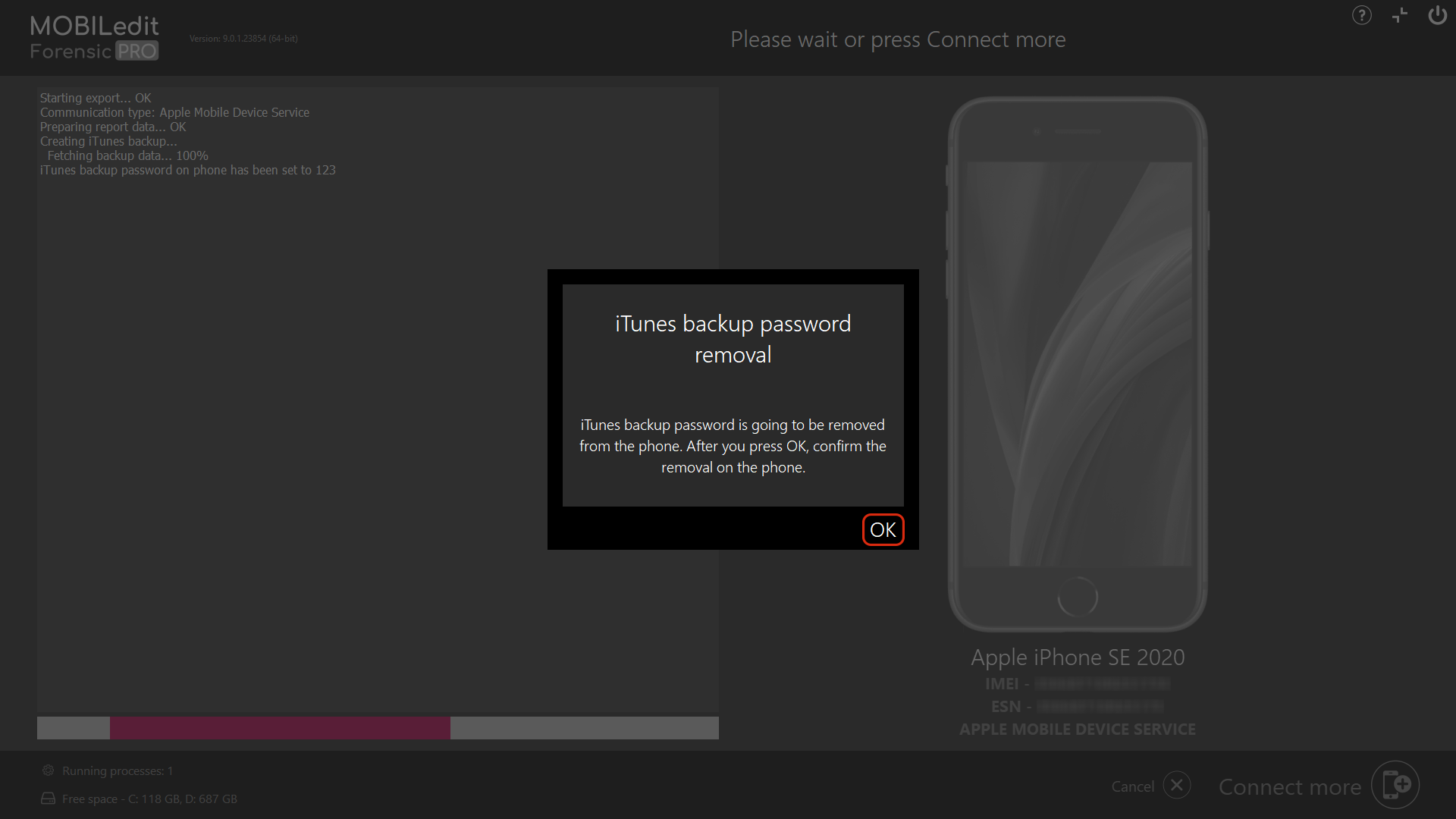
After the extraction, the password setting is removed.
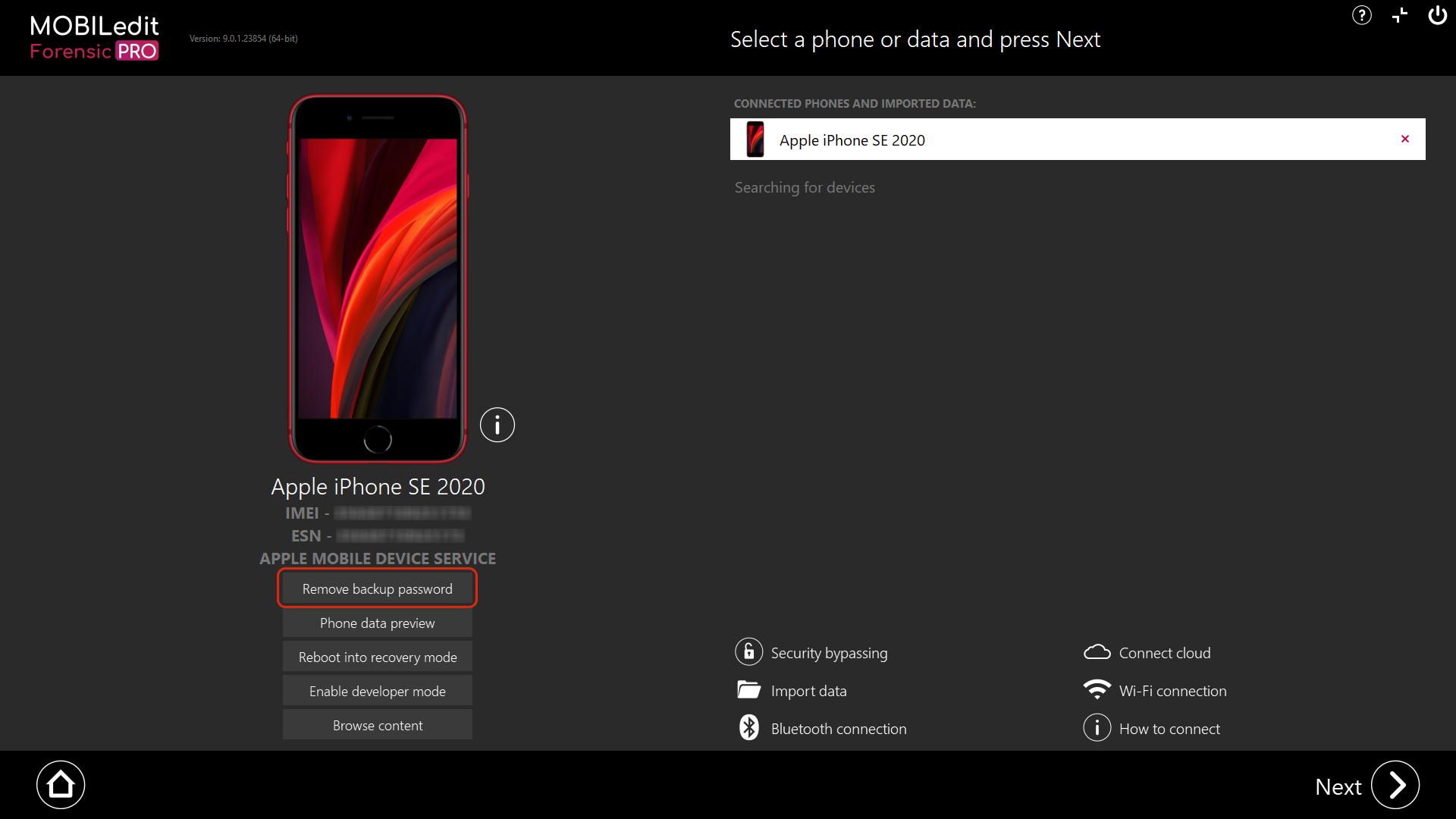
If the extraction is cancelled for any reason or, if the iTunes backup password is not removed, there will be a button to remove the password on the connection page below the device.
For iOS 16.1 and above, removing the backup password will also have to be confirmed by entering the lock screen PIN/password on the device.
The difference between an encrypted and unencrypted iTunes backup is:
Encrypted vs. Unencrypted iTunes Backups — Data Comparison
Category | Unencrypted Backup | Encrypted Backup | Notes / Forensic Relevance |
|---|---|---|---|
Basic Device Info | ✅ | ✅ | Includes device name, iOS version, serial number, UDID, IMEI, and installed apps list. |
Contacts, Call Logs, SMS/iMessage, Notes | ✅ | ✅ | Core user data is included in both. |
Photos and Videos (Camera Roll) | ✅ | ✅ | Both include media if "Include photos" is selected. Metadata may differ slightly. |
App Data (most apps) | ✅ | ✅ | App containers are included, but some secure apps store sensitive data only in encrypted backups. |
Health Data (HealthKit) | ❌ | ✅ | Exclusive to encrypted backups. Vital for investigations involving fitness, sleep, location, or step data. |
Keychain (Wi-Fi, website, and app passwords) | ❌ | ✅ | Exclusive to encrypted backups. Contains saved Wi-Fi passwords, email creds, etc. |
Website History & Safari Autofill Passwords | ✅ (partial) | ✅ (full) | Only encrypted backups include saved passwords and full autofill data. |
Apple ID Tokens, Wi-Fi settings, VPN profiles | ❌ | ✅ | Important for identifying connected networks and account tokens. |
Screen Time & Restrictions Passcodes | ❌ | ✅ | Useful for parental control or MDM-related cases. |
Device Pairing Records (trust relationships) | ✅ | ✅ | But encrypted backups include more pairing and trust data (handy for device linkage analysis). |
Mail Account Settings (but not messages) | ✅ | ✅ | Email account configuration is backed up, not the actual mail content. |
Safari Bookmarks, Tabs, History | ✅ | ✅ | Safari syncs with iCloud too, so verify overlap. |
Wi-Fi Networks (SSID list) | ❌ | ✅ | Networks previously connected to are recovered only from encrypted backups. |
Bluetooth Pairing Info | ❌ | ✅ | Identifies connected devices such as wearables, vehicles, or peripherals. |
Call History – Deleted Calls | ✅ (partial) | ✅ (full) | Encrypted backups often retain deleted entries for longer. |
HomeKit Configuration | ❌ | ✅ | Includes smart home devices and automation data. |
Apple Watch Pairing and Activity Data | ❌ | ✅ | Essential for smartwatch-related data. |
Messages (Attachments, Threads) | ✅ | ✅ | Both contain the SQLite message databases. |
Voice Memos | ✅ | ✅ | Same across both. |
Wallet & Payment Data | ❌ | ✅ | Contains tokenised payment data, not full card numbers. |
Saved Wi-Fi & VPN Passwords | ❌ | ✅ | Keychain-dependent. |
MDM Profiles and Certificates | ✅ | ✅ | But encrypted contains full certs and trust chains. |
